NOTE: An update to the CMMC, known as CMMC 2.0, was released in November 2021.
Learn more about CMMC 2.0 compliance by reading our dedicated blog.
The Cybersecurity Maturity Model Certification (CMMC) is a set of standards issued by the United States Department of Defense (DoD). Designed to improve cybersecurity across the Defense Industrial Base (DIB), the CMMC aims to ensure that sensitive information isn’t compromised by data spills or cyberattacks when being handled by contractors.
Here we will provide an overview of the CMMC and clarify who must comply with the certification. We will then examine the 5 levels of the CMMC framework, before explaining how companies can successfully comply with the regulation.
The CMMC in a Nutshell
- When?
Version 1.0 of the CMMC was released by the U.S. Department of Defense on 31 January 2020. The DoD started to issue a limited number of requests for low-level compliance from September 2020, but it’s expected that the CMMC requirements will be mandatory to follow in all cases from 2026 onwards. - Who?
The CMMC is applicable to all companies that carry out work for the U.S. Department of Defense. This includes both primary contractors that work directly with the DoD, as well as subcontractors that are hired by primary contractors to complete the work. - How?
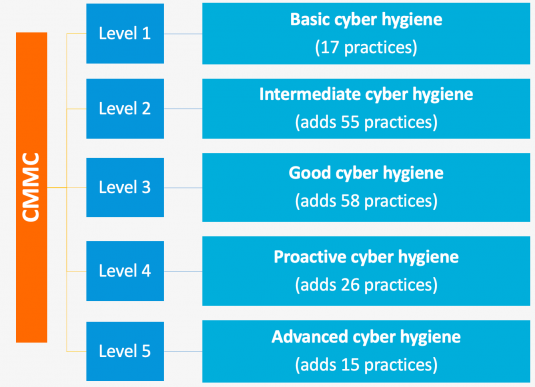
How does the CMMC work, exactly? Well, it’s split up into 5 certification tiers that reflect different levels of a company’s ability to protect classified government information. Each tier adds a new level of security that contractors must comply with in order to work with increasingly sensitive data.
Let’s take a closer look at the 5 levels of the CMMC framework:
The CMMC Framework
- Level 1:
Companies must perform “basic cyber hygiene” practices to protect Federal Contract Information (FCI) from cyberattacks and inside threats. FCI is “information, not intended for public release, that is provided by or generated for the government under a contract.” Basic cyber hygiene practices are required to be performed, but no documentation of processes and practices is required.
- Level 2:
Organizations are required to perform “intermediate cyber hygiene” practices, as well as document these practices and ensure they are available for reference. Companies must also implement a Systems Security Plan to aid their CMMC compliance efforts.
- Level 3:
Level 3 is the minimum requirement for contractors and subcontractors if they want to work with the DoD. So, this level likely applies to most businesses. Organizations are required to establish and maintain a plan that demonstrates they are managing “good cyber hygiene” practices.
To reach CMMC level 3, companies also have to protect Controlled Unclassified Information (CUI). Laws, regulations, and government-wide policies require safeguarding or dissemination controls for CUI.
- Level 4:
Level 4 requires organizations to have “proactive cyber hygiene” practices, which involves reviewing and measuring the effectiveness of practices and taking corrective action when necessary.
Companies must also protect CUI from Advanced Persistent Threats (APTs), which are types of cybersecurity attacks that use sophisticated hacking techniques to gain access to systems for prolonged periods of time.
- Level 5:
Companies are required to have “advanced cyber hygiene” practices, which means that standardized and optimized processes must be in place across the organization. In addition, businesses must implement practices that provide enhanced protection against APTs. Level 5 has 15 more additional practices compared to level 4, including establishing a cyber incident response team, running data forensics activities and analyzing network traffic. Obviously, this level demands significant preparations, investments and time.
BCWipe for CMMC Compliance
Starting from level 1 of the framework, the CMMC lists media sanitization as a necessary practice for securely removing sensitive information. By permanently removing data that’s stored on an electronic device, media sanitization ensures that confidential information is unrecoverable. To help your company with its CMMC compliance efforts, Jetico offers BCWipe Total WipeOut as a media sanitization solution that securely wipes entire drives beyond forensic recovery.
In addition to permanently removing all data from traditional hard drives, solid-state drives (SSD) and Non-Volatile Memory express (NVMe) drives, Jetico also offers BCWipe to erase selected data on active systems. Wiping individual files on SSD can be performed efficiently using BCWipe’s Reserved Space Manager, saving significant time for wiping free space by preserving previously wiped space in a clean state.
To comply with level 2 and above of the CMMC framework, Enterprise Editions of BCWipe and BCWipe Total WipeOut allow you to document your media sanitization with customizable wiping reports. Enterprise Editions equip administrators with central management of all wiping activities to further strengthen protection against data spills.
To get started with Jetico’s data wiping solutions, begin your free trial of BCWipe or BCWipe Total WipeOut today. To find out more about securely erasing hard drives, check out our ultimate guide.
Related Articles
Data Sanitization 5 Common Myths
Hardware Decommissioning Process: A 5-Step Checklist
IRS Publication 4812 & How to Comply with Wiping Standards
DoD 5220.22-M Explained – Data Erasure Standards
NIST SP 800-88 Guidelines for Media Sanitization Explained
How to Securely Wipe Your Windows 11 Computer Clean
The Ultimate Guide to Deleting Files Permanently
How to Delete Files on SSD
