BestCrypt Volume Encryption
Encrypt Hard Drives to Protect Data Stored on Fixed & Removable Devices
Protect data from physical threats (stolen computers, lost drives)
Encrypt hard drives for compliance (GDPR, HIPAA, PCI DSS)
No backdoors
Industry-best firmware support (UEFI, GPT, RAID)
Added resilience against cyberattacks

Explore BestCrypt Volume Encryption Features
Key features, language options and system requirements for encrypting hard drives.
**Enterprise users can take advantage of central management capabilities included in the Enterprise Edition of BestCrypt Volume Encryption.**
Fast Drive Encryption with 256-Bit
BestCrypt Volume Encryption delivers powerful protection for all sensitive data stored on drives.
- Secure Every Sector & Volume
Protects all sectors of your hard drive, including the operating system and system files, while encrypting both fixed and removable drives.
- Industry-Strongest Encryption Algorithms
Utilizes advanced encryption algorithms like AES-256, ARIA, Camellia, Serpent and Twofish, implemented with maximum key sizes and the secure XTS encryption mode. - Enhanced System Security
Includes secure hibernation to lock and protect your system, even during sleep mode.
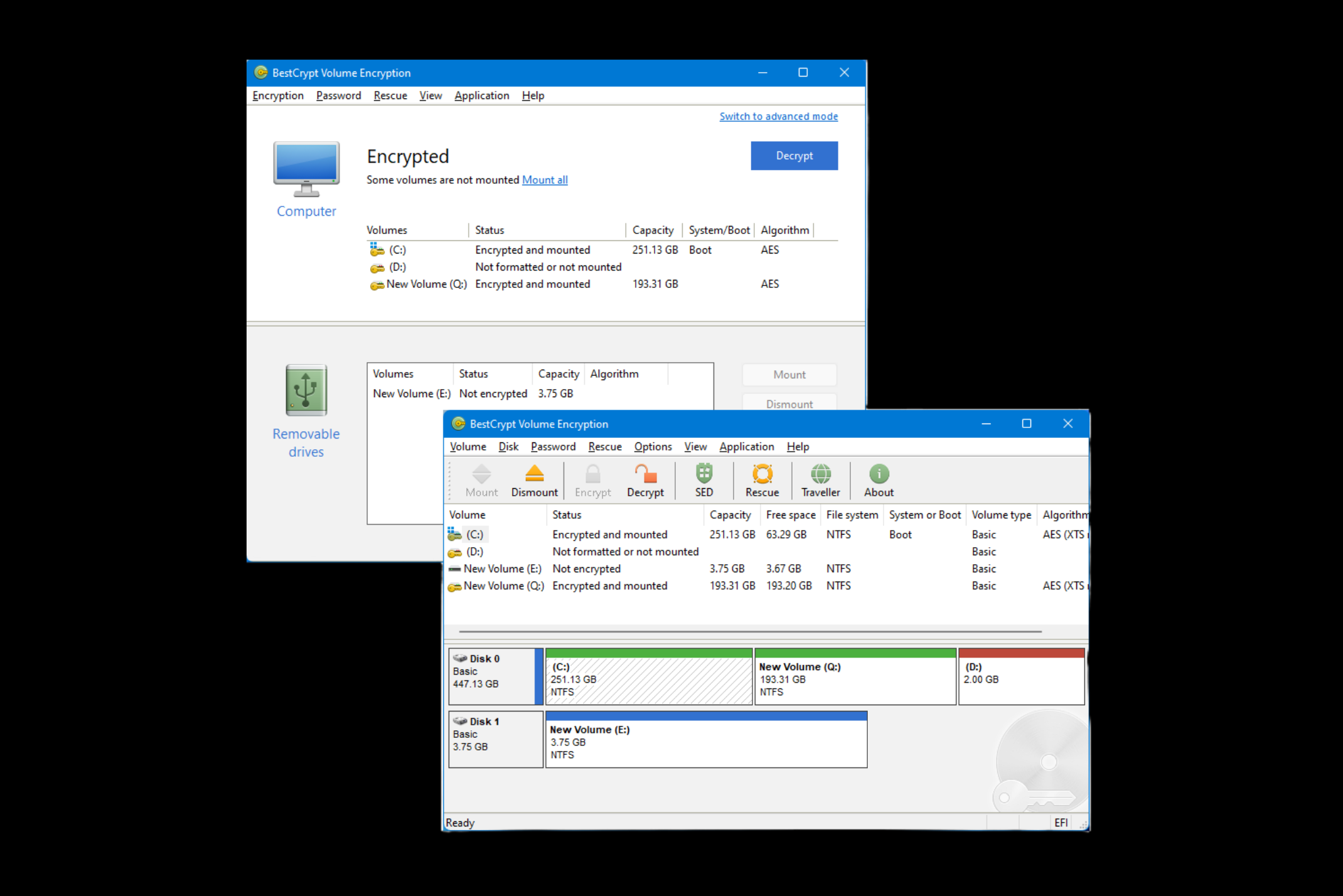
Robust Authentication for Enhanced Security
BestCrypt Volume Encryption offers advanced authentication features to ensure only authorized users can access encrypted data.
- Pre-Boot Authentication
Block access to the computer before the operating system starts, requiring the correct password to proceed. - Multi-Factor Authentication (MFA)
Add an extra level of protection by combining passwords with USBs, TPM, smart cards or hardware tokens. - Single Sign-On
Streamline access by automatically logging into Windows with your encryption password.
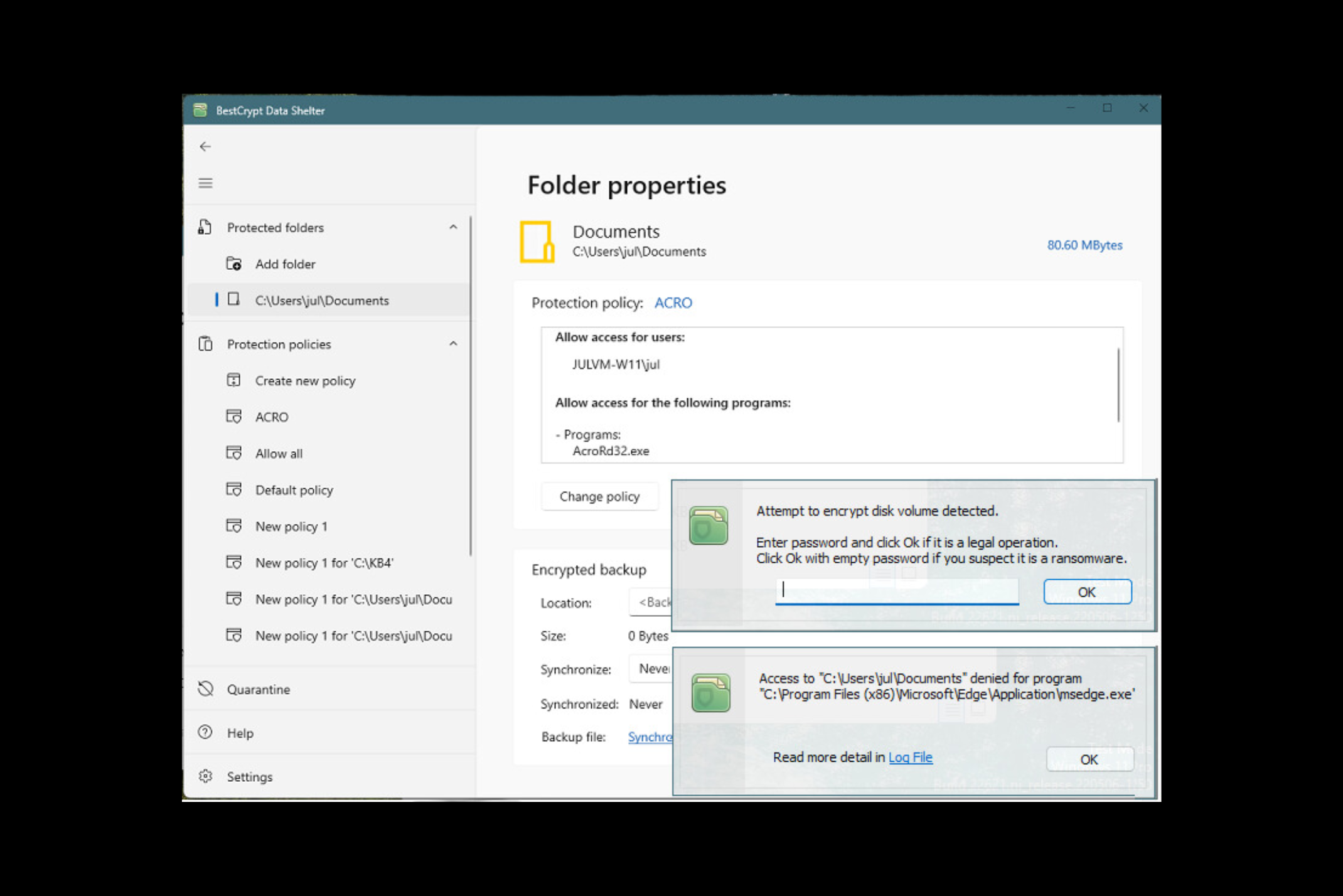
Active Protection Against Cyber Threats
BestCrypt Data Shelter provides an added layer of defense for your most sensitive files and folders, ensuring protection against active cyber threats. BestCrypt Data Shelter safeguards your data even while it’s in use by:
- Filtering out malicious processes to prevent unauthorized programs from accessing your files
- Restricting access to sensitive data by unauthorized users or applications
- Monitoring hacking attempts to keep track of potential breaches in real-time
Included as part of BestCrypt Volume Encryption, this tool also shields your files from crypto-malware, preventing encryption by ransomware attacks and keeping your information secure.
English
Jetico is responsible solely for the English language version of our software. However, many dedicated users worldwide have generously contributed translations, allowing the software to appear in their native languages.
If you would like to translate BestCrypt Volume Encryption into your native language, contact us.
Alternative languages (does not apply to Jetico Central Manager and only available for Windows)
We deeply appreciate our global community of committed users and are pleased to offer these user-contributed translations:
BestCrypt Volume Encryption supports the following operating systems:
Windows
Windows 11
Windows 10
Windows 8
Windows 7 SP1
Windows Vista (x86)*
Windows XP (x86)*
Windows Server 2019
Windows Server 2016
Windows Server 2012
Windows Server 2011
Windows Server 2008 R2
Windows Server 2003 (x86)*
(32- and 64-bit versions, unless stated otherwise)
*For legacy OSes, including Windows XP (x64), Windows Vista (x64), Windows Server 2003 (x64) and Windows Server 2008 (x64), use this version: BestCrypt Volume Encryption for legacy OS
Mac
macOS X 10.9 and later
Discover All Functionalities of BestCrypt Volume Encryption
Explore the full range of features that make BestCrypt Volume Encryption a powerful solution for encrypting hard drives:
Encrypt Every Sector, Including the Entire OS
Protect your entire operating system by encrypting the boot volume and the volume where system files are stored, ensuring complete security for all sectors and stored data.
Encrypt All Types of Volumes on Fixed & Removable Disks
Secure data on both fixed and removable disks, including external drives, with robust encryption for all types of volumes.
Strong Encryption Algorithms for Maximum Security
BestCrypt Volume Encryption uses robust encryption algorithms, including AES, ARIA, Camellia, Serpent and Twofish, all implemented with the largest key sizes defined by their specifications. These algorithms are supported with the highly secure XTS encryption mode, ensuring top-level data protection.
Support for Secure Hibernation
Ensure your encrypted data remains protected during hibernation with secure encryption that locks down your system and requires authentication upon wake-up.
Scalable Disk Encryption
Choose to encrypt your entire computer, specific disk volumes or a single volume – either fully or just the disk space occupied by files.
Start OS Only with the Right Password (Pre-Boot Authentication)
Prevent unauthorized access by requiring password authentication before the operating system even starts.
NEW: International characters are now supported, increasing character variety and making password attacks more difficult.
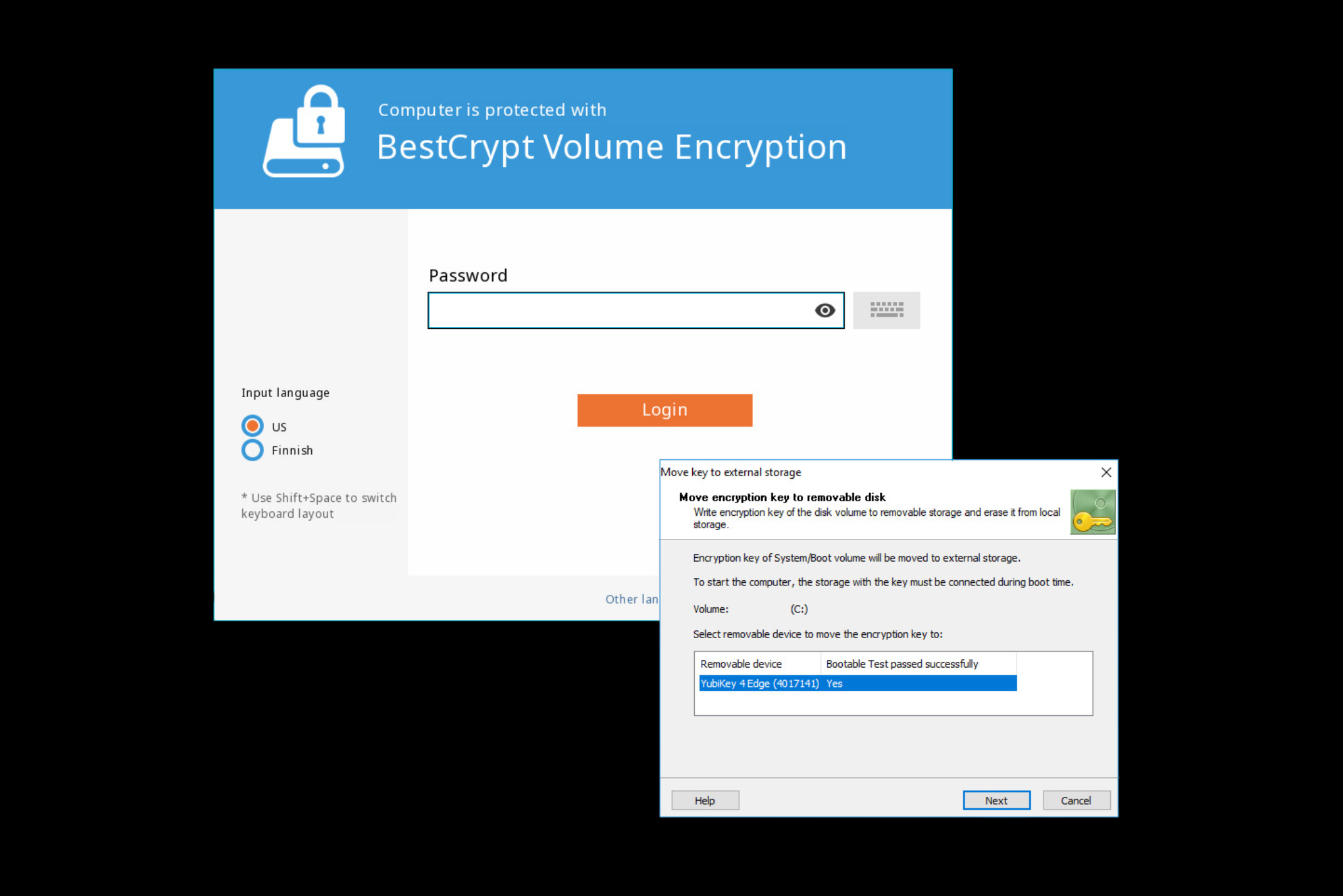
Rely on Multi-Factor Authentication (USBs, TPM & Hardware Tokens)
Enhance security with multi-factor authentication, combining passwords with USBs, TPM or hardware tokens like Yubikey, SafeNet eToken, PKCS #15-compliant smart cards and crypto tokens. BestCrypt Volume Encryption also supports secure hardware storage of encryption keys on regular removable disks.
Support for Single Sign-On
Streamline access with Single Sign-On by seamlessly using your encryption password to automatically log in to Windows.
Need More Details or a Hands-On Experience?
Explore how BestCrypt Volume Encryption can meet your needs. Contact us for a free trial or to request a personalized demo today!
News & Blogs
Stay updated with the latest news, insights, trends and expert tips on data protection and cybersecurity.
Check back here regularly for news and blogs


