Are you worried about your data being safe in case your PC gets lost or stolen? In this guide we will teach you how to encrypt your computer with BestCrypt Volume Encryption. This might sound like a complicated process, but it really isn’t.
If you haven’t yet installed BestCrypt, see our easy 3-step guide.
Looking for a more user-friendly way to deal with encryption? Review step-by-step instructions on how to encrypt your PC with ‘Simple Interface’.
Step 1: Run as Administrator
Once you have the program installed, start BestCrypt Volume Encryption by clicking on the icon in the bottom right of your screen in the system tray. Then choose the option ‘as Administrator’ to make the required changes to your computer.
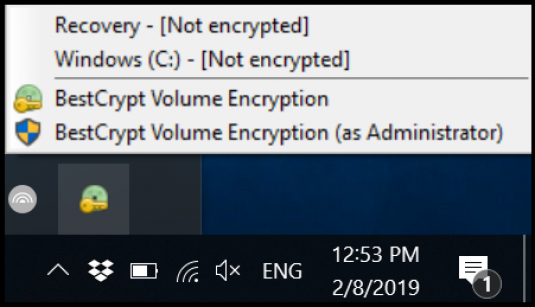
Or you can open the program and then choose to ‘Run as administrator’.
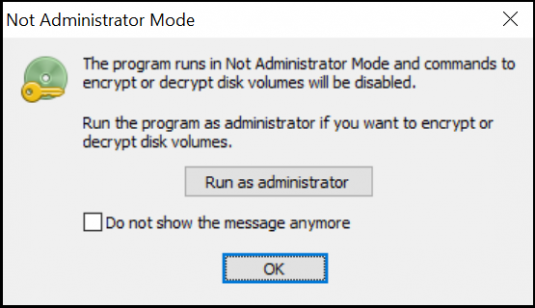
To be able to encrypt the computer, you will need to give access for BestCrypt to make the required changes to the computer. When asked, click ‘Yes’.
Step 2: Choose disk to encrypt
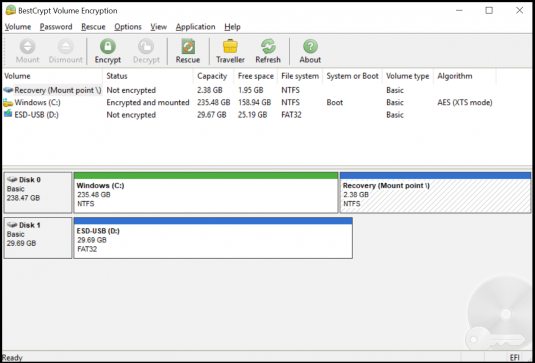
In the BestCrypt Volume Encryption main window you can see the volumes on your device and their encryption status: ’Not encrypted‘, ’Partially encrypted’ or ’Encrypted‘. The listed volumes represent where the data on your computer is stored. If you have any other disk encryption software running, make sure to exit them to avoid conflicts.
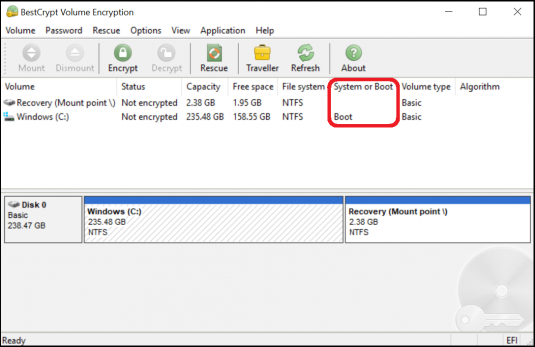
To encrypt your computer with better safety than just the basic user login, you will need to encrypt the volume from which the device boots or starts up. Most likely, your boot volume is Windows (C:). This can be checked from the ‘System or Boot’ column as shown. To start the encryption process, double-click the boot volume.
Step 3: Choose encryption password
Enter a unique password. This password will be asked every time you turn on your computer. BestCrypt also helps you determine the strength of your password as you are typing. Make sure to create a memorable password! If you need help, check out our blog.
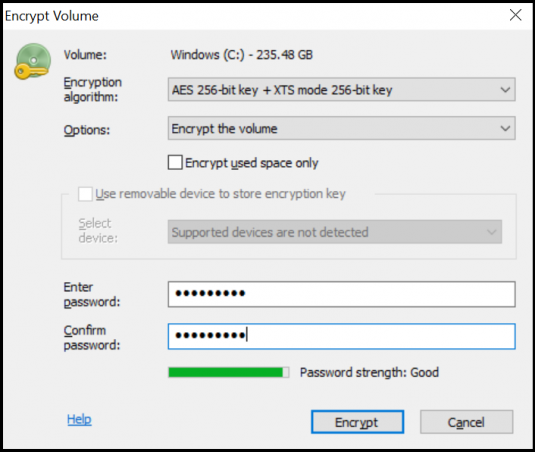
When you are ready, click ‘Encrypt’.
Step 4: Hard drive encryption process
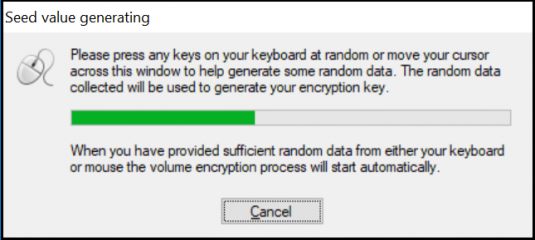
For the hard drive encryption process, you will only need to help in creating random data for the encryption seed. The
so-called ‘seed data’ is needed to generate a random encryption key. To get random data for the seed, the program will display a dialog window, visualizing the encryption seed generation process. Move your mouse around inside this window, or type anywhere on the keyboard to generate random data.
Once the encryption key has been generated and the window closes, you will be shown the encryption progress status. The time it will take to complete depends on the size of the volume and the processing power of the computer. In our example, encrypting a 235 GB volume took 40 minutes. For 500 GB, the encryption process will usually take a little over an hour.
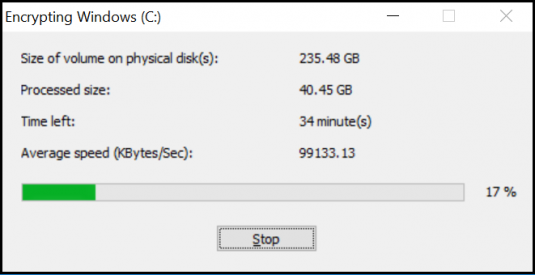
To pause the encryption process, you can always click ‘Stop’ and continue later.
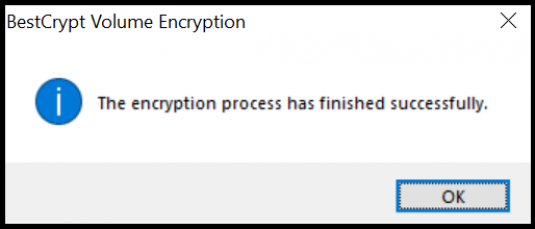
The following prompt is displayed once the encryption has successfully completed. If something else happens, please contact Jetico Technical Team.
Step 5: Create Rescue Disk
When the process completes or is paused, you will be prompted to make a Rescue USB or ISO (CD) – do not ignore this message! We recommend going through the Rescue Disk preparation process immediately and keeping it updated whenever prompted. A Rescue Disk is important to create in case your computer hardware malfunctions. If necessary, your computer can be started from the Rescue Disk instead of the original drive.

Follow our Rescue Disk creation guide. When your Rescue Disk is ready, just restart your computer.
Step 6: Restart and enter password
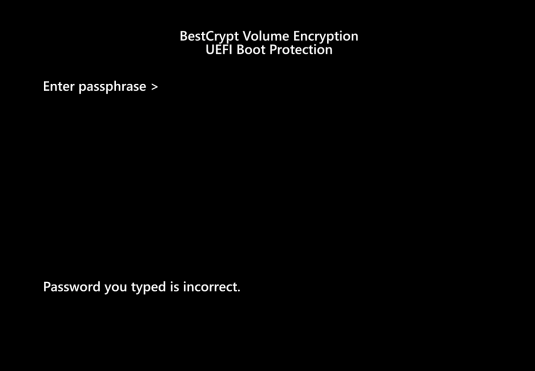
When rebooting, you will see a pre-boot authentication screen. Type in the password you chose earlier, and press ’Enter‘. Now your computer will continue the normal start up process.

If an incorrect password is entered, the pre-boot authentication screen will show the following message
’Password you typed is incorrect’.
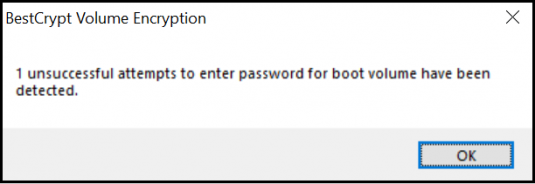
Upon logging in with your encryption and user passwords, you will be notified of any unsuccessful login attempts
(including mistyped passwords).
There it is! Your computer is now safely encrypted with BestCrypt.
If you have questions, you can always contact us!
