If you’re part of a company or organization based in Saudi Arabia, then you are probably wondering how you can comply with the new regulations introduced by the Saudi Arabian Monetary Authority (SAMA). Understanding all requirements can be a lot to unpack. In this blog we’ll focus on ‘Secure Disposal of Information Assets’ and share 3 steps on how to implement a successful SAMA compliance strategy.
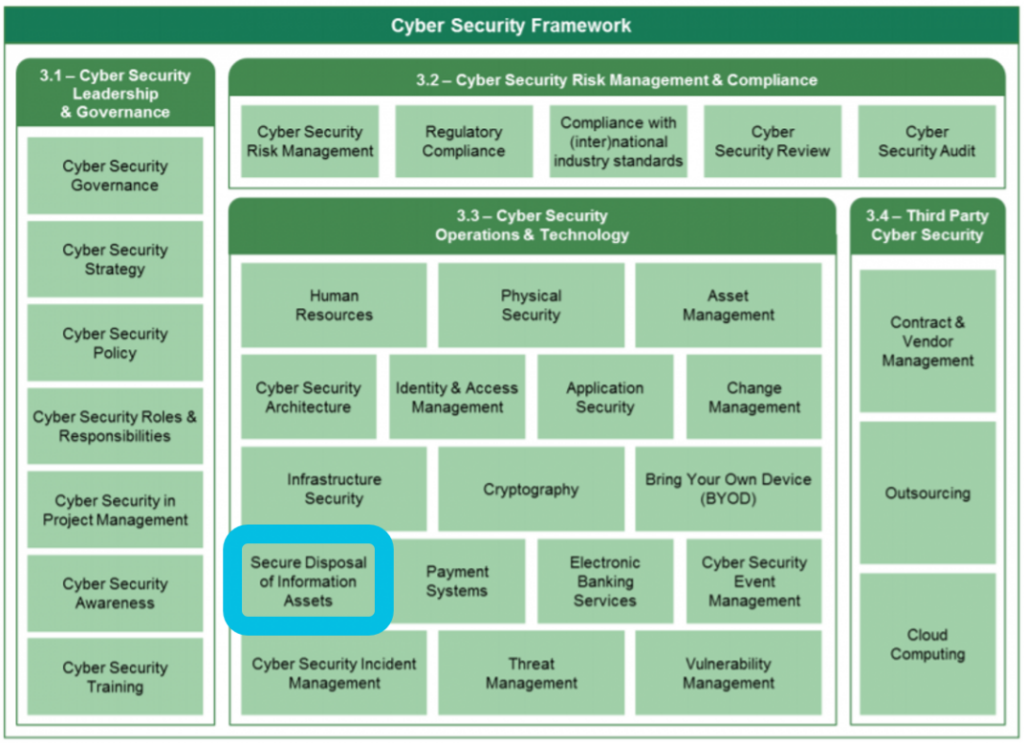
SAMA in a Nutshell
- When?
The SAMA regulations came into effect in May 2017. - What?
When we refer to the SAMA regulations, we are talking about the Cyber Security Framework that was issued by the Saudi Arabian Monetary Authority (SAMA). The framework is based on international cybersecurity standards and its objective are to:
1. Create a common approach for addressing cyber security.
2. Achieve an appropriate maturity level of cyber security controls.
3. Ensure cyber security risks are properly managed. - Who?
The Cyber Security Framework is mandatory for all financial institutions operating in Saudi Arabia, including:
– Banks
– Insurance and reinsurance companies
– Financing companies
– Credit bureaus
– The Financial Market Infrastructure
All member organizations are “subject to a periodic self-assessment”, which will then be “reviewed and audited by SAMA to determine the level of compliance with the framework”.
What Does SAMA Say about Data Wiping?
Now that you’ve learned a little more about SAMA, it would be helpful to know exactly what the regulations say about data wiping. In short, SAMA states that organizations must securely and permanently dispose of sensitive data when it’s no longer needed. Below we will take a look at what the regulations say in more detail:

Prepare for SAMA Compliance
By taking these 3 steps, you’ll ensure that your organization is ready to comply with SAMA wiping requirements both now and in the future.
- Understand where your data resides
It’s your responsibility to know where your data is, even if you outsource data storage to a cloud provider. Map your data flows and build a clear picture of where your information is located, how it is being accessed, and how it is being shared. When the time comes, finding the information to erase will be much faster and easier. - Classify and get organized
After determining where your data resides, it’s crucial to get (and stay) organized. Start by creating an inventory – classify data by importance to your company and by level of risk. It’s also a good idea to put someone formally in charge of data protection. This sends a message to your consumers (and compliance officers) that you take the protection of their data seriously. - Use the right tool
The kind of data you need to erase will help determine what type of software is best for your organization. For example, if you have sensitive information on a computer that’s no longer needed, then you should invest in software that can completely wipe your hard drive before it’s repurposed or disposed. However, if you have a specific file or folder residing somewhere it shouldn’t, then you’ll want to use a tool that lets you wipe selected data from an active computer, while keeping the rest of your files and programs intact.
How Data Wiping Works
The most secure and effective way to dispose of your information assets is by wiping, or overwriting, the relevant data when it’s no longer needed. As we all know, the act of permanently removing data from a hard drive isn’t as simple as emptying the recycle bin. Information saved to a hard drive leaves behind residual data, or data remanence, even after the files have been deleted by normal means. In order to stop this data from being restored and accessed with widely available file recovery software, you can choose to wipe your data and permanently erase your information.
If you want to learn more about securely wiping your data, check out our ultimate guide.
