BestCrypt Data Shelter
Data in Use Protection to Lock Down Active Files from Ransomware & Cyber Threats
Protect selected folders from unauthorized access – including ransomware
Create & apply flexible protection policies for multiple folders
Detect & automatically block suspicious or untrusted processes

Explore BestCrypt Data Shelter Features
Explore BestCrypt Data Shelter’s key features, language options and system requirements for protecting data in use.
Custom Protection Policies
With BestCrypt Data Shelter, users can set up custom protection policies to secure the contents of any chosen folder. Once a policy is applied, the folder and its files are shielded from unauthorized users and applications when accessed, helping prevent unwanted modifications or exposures.
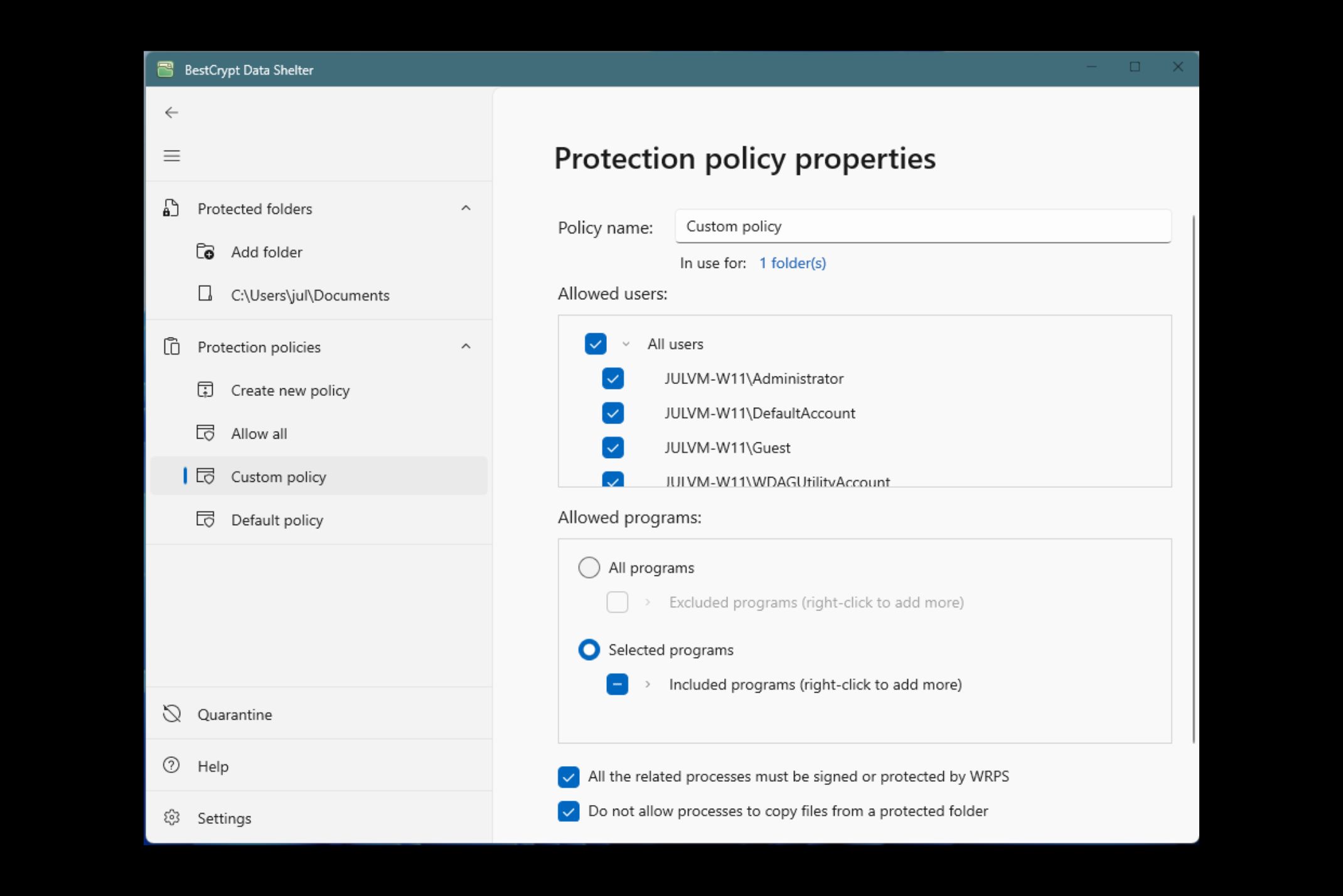
Fine-Tune Access Controls
BestCrypt Data Shelter’s flexible protection policies allow you to determine which programs and users can access specific folders. Choose from manual configuration to grant access to select programs, or allow Data Shelter to automatically register trusted programs based on usage history. This customizability ensures sensitive files remain accessible only to verified programs and users.
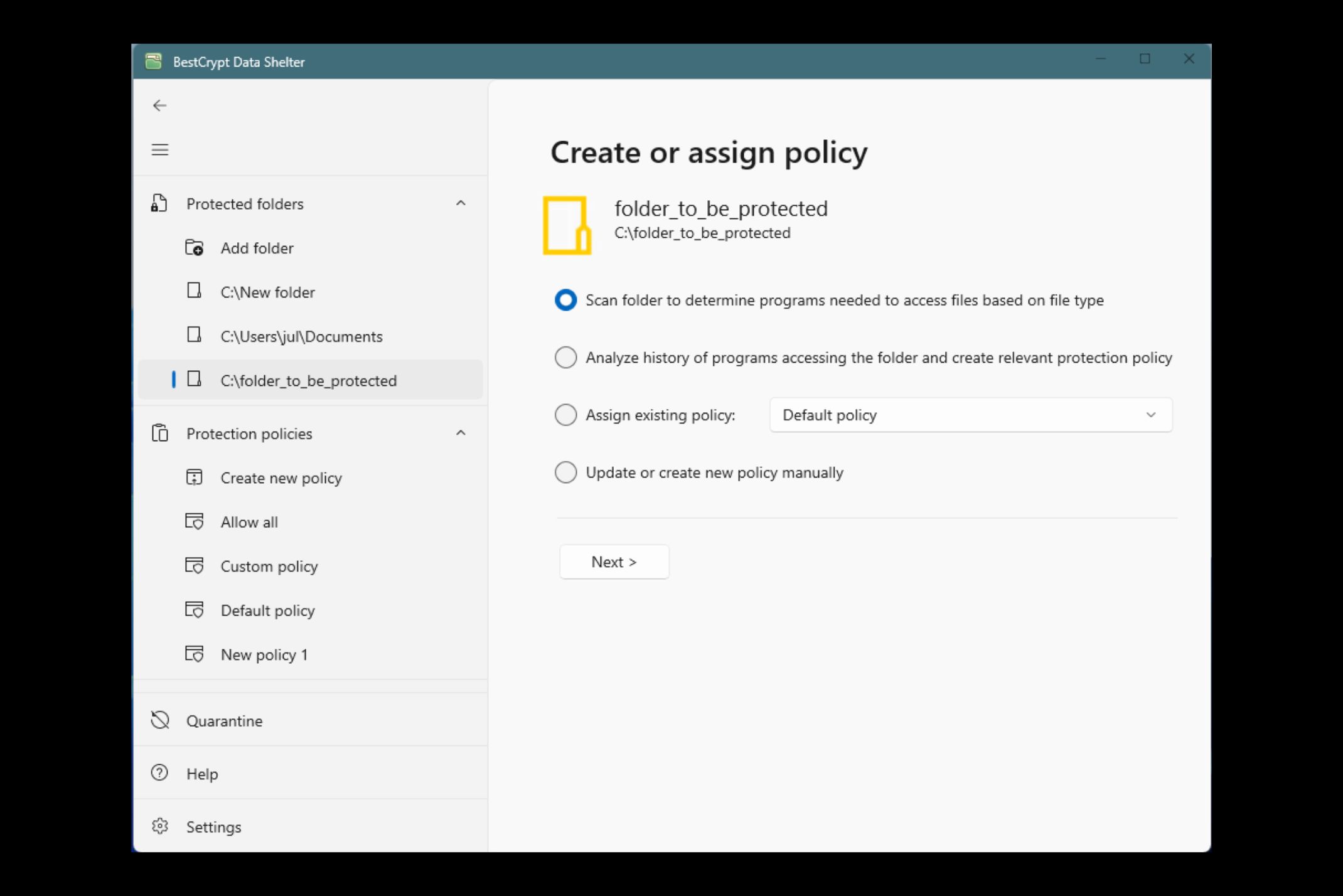
Enhanced Malware & Ransomware Protection
Safeguard your data from advanced threats with built-in defenses against malware and ransomware. BestCrypt Data Shelter continuously monitors protected folders for suspicious activity, offering proactive protection by stopping malicious processes before they can compromise sensitive information.
English
If you would like to translate BestCrypt Data Shelter into your native language, contact us.
BestCrypt Data Shelter supports the following operating systems:
Windows
Windows 11
Windows 10
Windows 8/8.1
Windows 7
Windows Vista
Windows XP
Windows Server 2016
Windows Server 2012
Windows Server 2011
Windows Server 2008
Windows Server 2003
(32- and 64-bit versions, unless stated otherwise)
Discover All Functionalities of BestCrypt Data Shelter
Review the full range of features that make BestCrypt Data Shelter a powerful tool for data-in-use protection:
Abnormal Process Detection
Identify and terminate any unusual processes within protected folders, blocking suspicious activity in real time.
File Copy & Move Restriction
Prevents files from being copied or moved from a highly protected folder to one with lower security settings, reducing the risk of unauthorized data exposure.
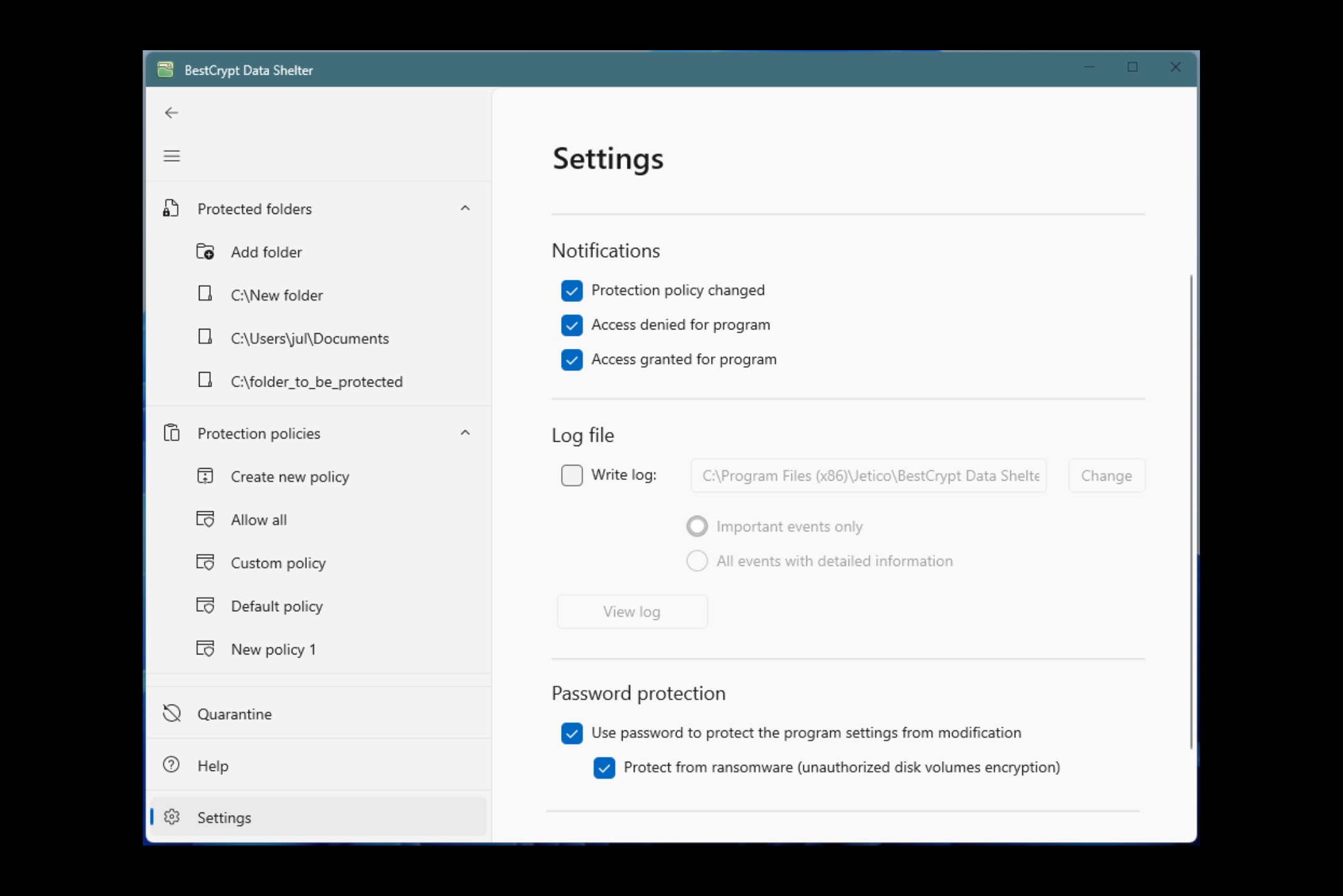
Password-Protected Settings & Policies
Restricts access to protected folders even if an attacker gains administrator credentials. Protection policies cannot be bypassed without the right password, ensuring that ransomware or unauthorized users cannot compromise security.
Activity Log Monitoring
View detailed log files that record the activity of processes in protected folders, helping administrators and users track access history for greater visibility and oversight.
Encrypt Drives with BestCrypt Volume Encryption
BestCrypt Data Shelter integrates seamlessly with BestCrypt Volume Encryption. Easily view whether protected folders reside on encrypted volumes and, if needed, secure the underlying disk with a single click using the ‘Encrypt’ button.
Compressed & Encrypted Backup Archives
Automatically create compressed and encrypted backups of your protected folders with Jetico’s BCArchive software, embedded directly in BestCrypt Data Shelter. Users can set regular synchronization to keep backup archives up to date.
News & Blogs
Stay updated with the latest news, insights, trends and expert tips on data protection and cybersecurity.
Check back here regularly for news and blogs