BestCrypt Traveller
Access Encrypted Files Wherever You Are
Free add-on for licensed BestCrypt users
Access BestCrypt files on any Windows or Mac
Run without installation

Explore BestCrypt Traveller Features
Explore BestCrypt Traveller’s key features, language options and system requirements for seamless, secure access to your encrypted files.
Access Encrypted Files
BestCrypt Traveller can be downloaded from any place in the world and allows quick access to encrypted container files created by BestCrypt. A single BestCrypt Traveller executable can also be stored on a removable disk together with encrypted containers, which allows you to access the data on any computer that might be temporarily available during a trip. BestCrypt Traveller supports containers encrypted by any encryption algorithm and any key generator available in BestCrypt.
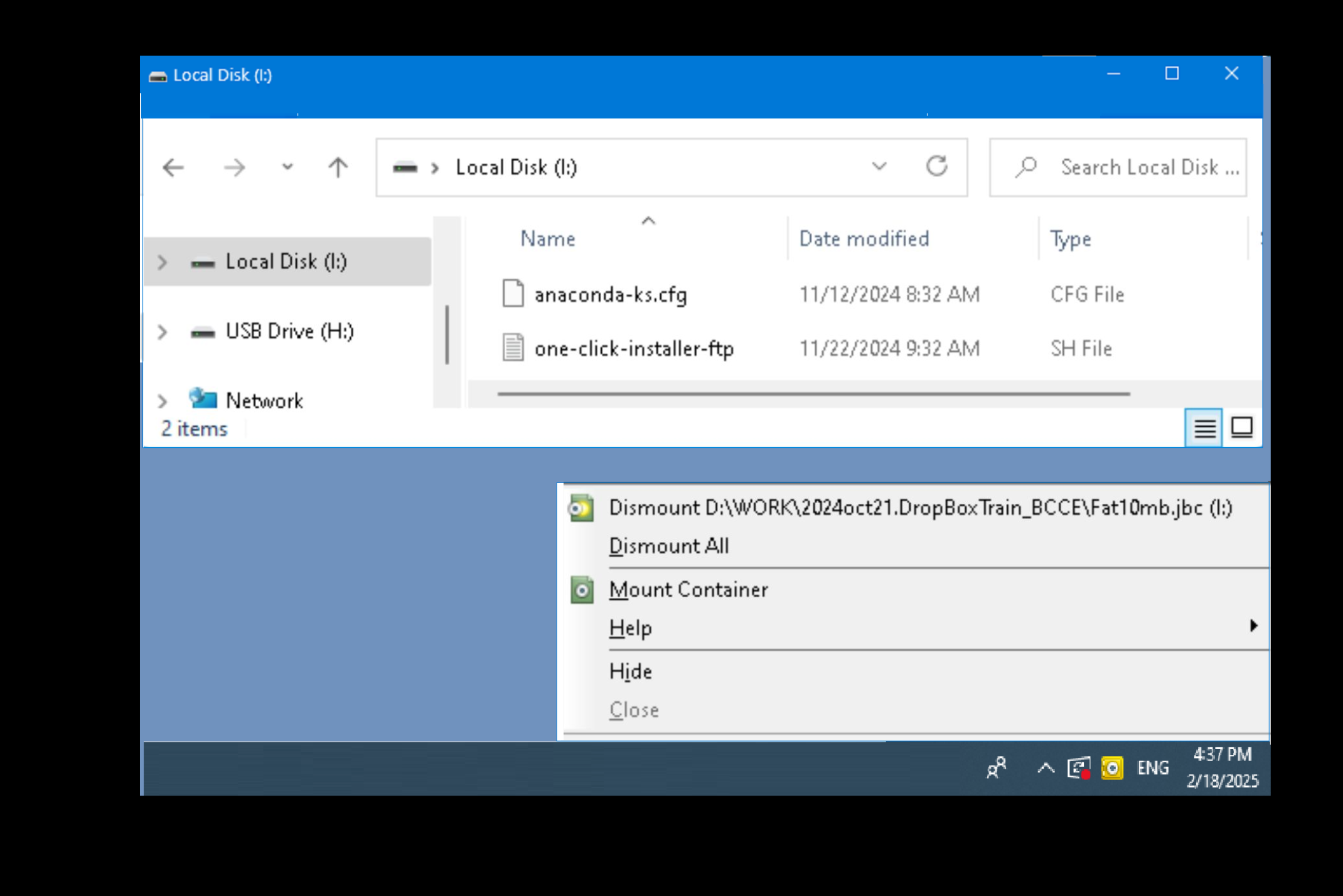
Run Without Installation
BestCrypt Traveller operates as a guest program, running directly from a single executable file without the need for installation (BCTraveller.exe for Windows, BCTraveller.dmg for Mac). Simply launch the executable and a BestCrypt icon will appear in the system tray, allowing you to mount or dismount encrypted containers easily. Once you’re done, BestCrypt Traveller leaves no traces behind, removing all usage information and keeping your activity completely private.
English
Jetico is responsible solely for the English language version of our software. However, many dedicated users worldwide have generously contributed translations, allowing the software to appear in their native languages.
If you would like to translate BestCrypt Traveller into your native language, contact us.
We deeply appreciate our global community of committed users and are pleased to offer these user-contributed translations:
BestCrypt Traveller supports the following operating systems:
Windows
Windows 11
Windows 10
Windows 8
Windows 7
Windows Vista
Windows XP
Windows 2008 Server
Windows 2003 Server
Mac
Mac OS X 10.7+
News & Blogs
Stay updated with the latest news, insights, trends and expert tips on data protection and cybersecurity.
Check back here regularly for news and blogs