It might have snuck up on us over the last few years, but today the concept of storing files in the cloud is an indispensable part of our working life. Data saved in the cloud, however, is not necessarily safe. Just like with files saved to our computers, data stored in the cloud can be leaked or stolen.
Using encryption for data saved to the cloud can provide assurance that none of our sensitive information will be read by third parties.
Here we’ll discuss the importance of encrypting data in the cloud and review some different encryption options. Finally, we’ll talk you through our best practices for companies that want to build a cloud encryption strategy.
Why Encrypting Data in the Cloud?
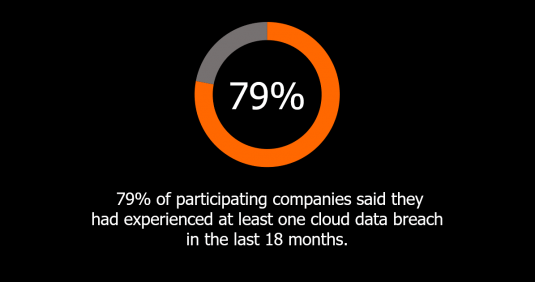
One reason why cloud encryption should be essential for companies is due to frequent data breaches on cloud services. According to a new survey conducted by Ermetic, 79% of participating companies said they had experienced at least one cloud data breach in the last 18 months.
Why Is the Cloud Vulnerable?
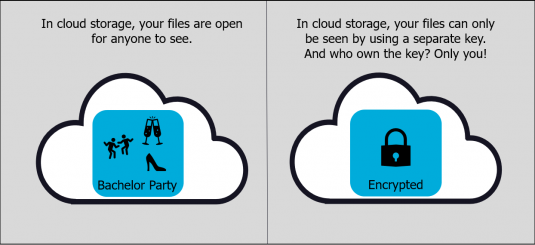
If you don’t use encryption to protect the data you save in the cloud, then your information is only protected by an online key. These online keys are the individual passwords that you enter in order to access your cloud account. Cloud providers store your online keys. If your cloud provider is hacked, your data will become accessible.
By hacking the server of one cloud provider, attackers can access the unencrypted data of millions of people and companies.

How to Properly Secure Your Files on the Cloud
The best way to ensure your cloud data remains safe is to encrypt your files. When data is encrypted before being uploaded to the cloud, you add an extra layer of privacy protection to your account – making data breaches much less likely. So even if your online account gets exposed, your encrypted files could still only be seen by entering the correct key, which cyber criminals would not possess – only you hold your own encryption keys.
Who Should Manage Your Keys?
When we talk about encryption keys, we’re referring to codes used by organizations or users to access and unscramble their encrypted files. Essentially, the keys are what will let you access your data, while making sure to block out prying eyes.
Considering the importance of encryption keys, it only makes sense that we discuss who manages them. Companies must ask themselves if they prefer the idea of paying extra fees to let cloud services manage their keys, or if they want to manage their encryption keys themselves.
How can you add an encryption key to your existing online account? There are 2 ways to go:
- Cloud service providers
Most of the major cloud service providers offer optional encryption services. Some common providers are Amazon Web Services, Microsoft Azure, and Google Cloud.
– Pros: Cloud service providers can manage your encryption keys for you, which takes some of the responsibility away from companies.
– Cons: There’s always the chance that your encryption keys will be under greater threats or perhaps mismanaged by cloud service providers. Data breaches involving Dropbox and iCloud still happened despite their own encryption. - Third-party security companies
Encryption solutions for storing cloud data are offered by third-party security companies. For example, BestCrypt enables you to protect your data in the cloud by securely storing files inside encrypted containers.
– Pros: Using third-party encryption software gives you control of your own keys and ensures that the privacy of your files won’t be compromised by another company’s mistake.
– Cons: You take on additional responsibility by managing your own encryption keys.
Best Practices for Encrypting Data in the Cloud
Now that you have a better idea about your choices when it comes to cloud encryption, let’s go through some best practices for putting together a cloud encryption strategy for your company.
- What type of data should you encrypt?
– You don’t need to encrypt all of the data that you upload to the cloud. What you should focus on encrypting is any sensitive data that pertains to your company or the personal information of your customers. This is especially important if the data falls under privacy legislation like GDPR. - When should data be encrypted?
– Encrypted data that you save to the cloud will be protected while it’s at rest. Yet it’s also important to encrypt sensitive data when it’s in transit. This will protect data when it’s being moved around to different locations. - What type of encryption should you use?
– There are 2 common methods for encrypting files with third-party software — locking down individual files one-by-one or storing many together at once inside encrypted containers. The first requires a unique password for each of your files. The second is much easier on the brain, requiring just one password per container. Here are instructions to use BestCrypt Container Encryption in the cloud. - Back up your data.
– In case your cloud data becomes corrupted or if you experience other accessibility or security issues, you must back up your data to an external hard drive. Of course, hard drives should also be encrypted to protect them from physical threats. Here we show you how to encrypt your external hard drives in 5 steps with BestCrypt Volume Encryption. - Encryption management.
– Administrators are advised to use an encryption solution that provides access control to company data. By controlling who can access which data, you can enforce a central policy and reduce the risk of ransomware locking up or modifying files. Key management is also an essential feature, empowering administrators to restore encryption keys when forgotten or maliciously changed. Options like BestCrypt Volume Encryption – Enterprise Edition also offer auditing solutions to aid compliance.
Now you’re on your way to put together your own encryption strategy for data saved in the cloud. If you’d like some more information on data encryption solutions for enterprises then be sure to check out this simple guide.
Happy Encrypting!
Looking for an alternative to Boxcryptor? Read 3 reasons why you should choose BestCrypt.
