The CCPA ‘Right to Delete’ is an example of how data protection regulations like GDPR and the LGPD empower individuals to take ownership of their personal information. These laws allow individuals to request the deletion of their personal data, granting them a level of control over it that was previously lacking.
For organizations, however, fulfilling an individual’s right to be forgotten is no simple matter. In particular, it can prove challenging due to the potential complexity of finding and erasing all personal data associated with an individual across your systems.
Focusing on the CCPA in particular, this blog will explain:

Let’s get started with an overview of the CCPA and its ‘Right to Delete’.
CCPA & the ‘Right to Delete’ in a Nutshell
- What?
The California Consumer Privacy Act (CCPA) was created to secure privacy rights for residents of California and is closely modeled after the General Data Protection Regulation (GDPR). Likewise, the ‘Right to Delete’ section of the CCPA has much in common with the GDPR’s ‘Right to Be Forgotten‘ (officially known as the ‘Right to Erasure‘), although the former is narrower in scope, applies primarily to businesses, and includes more exemptions. - When?
The CCPA was passed in 2018. In November 2020, Proposition 24 was approved, introducing additional privacy protections that came into effect in January 2023. - Who?
The CCPA applies to for-profit businesses operating in California that meet any of the following criteria:
– Have a gross annual revenue of over $25 million;
– Buy, sell or share the personal information of 100,000 or more California residents or households; or
– Derive 50% or more of their annual revenue from selling California residents’ personal information.
Challenges of Complying with the CCPA’s ‘Right to Delete’
Organizations face a few challenges when it comes to complying with the CCPA’s ‘Right to Delete’. These challenges can be grouped into 2 categories: identifying and locating personal data, and securely deleting it to ensure compliance.
1. Identifying & Locating Personal Data
Personal data is often scattered across a wide range of systems, including employee devices, cloud platforms, backups and archives. This fragmentation makes it difficult to locate all instances of an individual’s data.
The challenge is made trickier if you have legacy systems and multiple data storage solutions that are not designed for easy data retrieval or deletion. Backups and archives present a particular difficulty as they are created for data recovery, not modification, making it hard to ensure that deleted data is fully removed from these storage layers.
2. Securely Deleting Data for Good
Identifying data is the first step, but secure deletion is critical to compliance. Residual information may remain without using data wiping solutions, leaving businesses vulnerable to compliance risks. Deleted data can persist in fragmented forms posing potential security and regulatory threats.
To address these challenges, organizations need tools that not only locate sensitive data throughout all enterprise systems, but also ensure its secure and irreversible deletion.
Combining Search & Data Wiping to Comply with the CCPA’s ‘Right to Delete’
As mentioned in the previous section, using advanced search tools can help simplify compliance with the CCPA’s ‘Right to Delete’. One such tool is Search, a personally identifiable information (PII) and sensitive data discovery tool. Search is a new feature in BCWipe, Jetico’s software for wiping files beyond forensic recovery.
Advanced search tools can allow businesses to locate personal data spread across multiple systems, including local devices, cloud platforms and archives. Here’s 3 additional benefits of using an advanced search tool like BCWipe’s Search feature:
- Network-Based Search Capabilities
Organizations can efficiently scan for sensitive personal data across entire infrastructures, saving time and reducing errors. - Customizable Parameters & Smart Search Features
Advanced search tools enable businesses to tailor search parameters to locate specific types of PII, such as Social Security numbers, tax IDs and other unique identifiers. - Beyond Traditional File Formats
Search functions extend their reach to uncover hidden data, residual information in backups, and even sensitive content within non-traditional formats like images.
While identifying data is a crucial first step, pairing search tools with data wiping solutions gives organizations the ability to locate and irreversibly delete sensitive information with ease. This integration eliminates risks associated with partial deletions, where data remanence might remain in storage systems or backups.
Benefits of Using a Combined Approach
By combining robust search functionalities with advanced data wiping software, organizations can achieve comprehensive data management and ensure compliance with the CCPA. This integrated approach eliminates the need to transfer search results to a separate wiping tool, a process that is often time-consuming and prone to errors such as data incompatibility or upload failures. With an all-in-one solution, businesses can:
- Streamline operations
- Respond to deletion requests more efficiently
- Reduce the margin for error
Ultimately, this approach not only strengthens data protection strategies but also reduces the risk of non-compliance and enhances consumer trust.
3 Steps to Effectively Use Search & Wiping for Compliance
Let’s take a look at how this can be achieved in 3 easy steps:
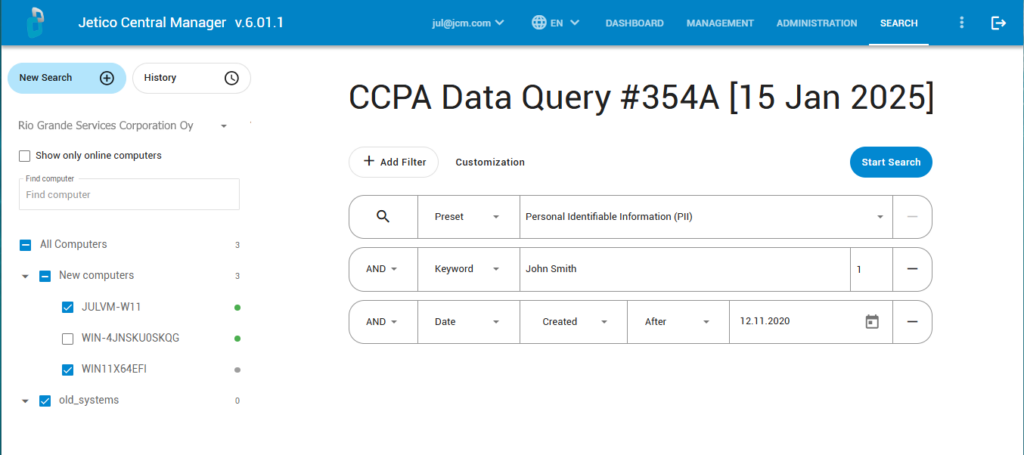
Step 1: Select PII Preset & Enter Keyword
BCWipe’s Search feature helps you find highly specific data. In this case, you are looking to find and delete personally identifiable information (PII) in order to comply with the CCPA’s ‘Right to Delete’.
Start by selecting the ‘Personal Identifiable Information (PII)’ preset and entering a relevant keyword, such as the name of the person that requested your organization to delete their data. In the following example, this person’s name is John Smith.
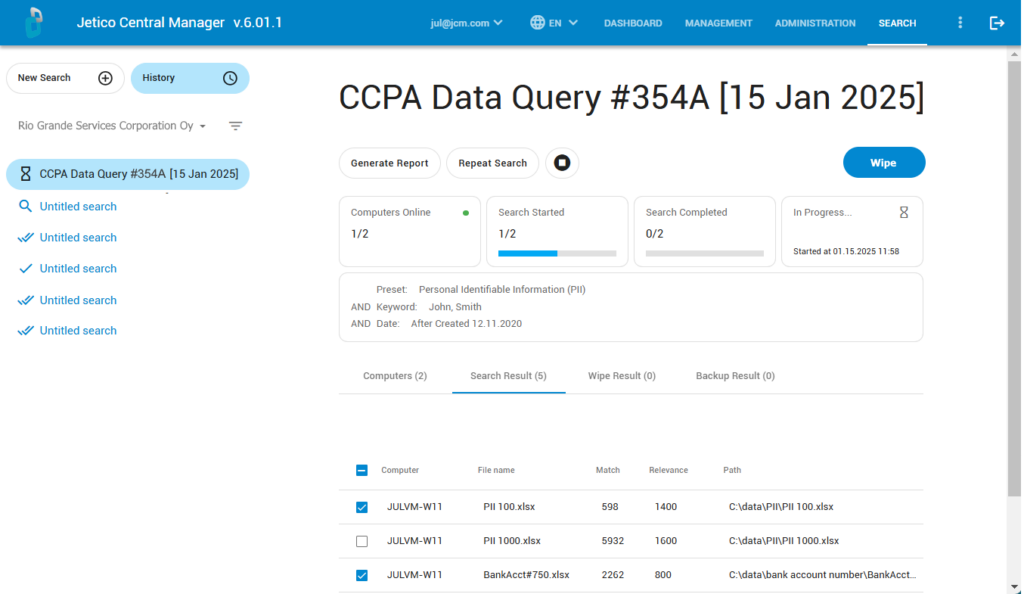
Step 2: Review Search Results
After the search is finished, all the files that contain PII relating to the keyword will be displayed in the ‘Search Results’ field. You can now review and verify these files before initiating deletion.
Step 3: Wipe Selected Files
Click the tick boxes next to the files you wish to permanently delete and then select ‘Wipe’ to begin the wiping process. Selected files will be deleted beyond forensic recovery with BCWipe, ensuring that you comply with the CCPA’s ‘Right to Delete’.
Best Practices & Key Considerations
In addition to using advanced search tools and trusted data wiping software, organizations could consider adopting the following best practices to help comply with the CCPA’s ‘Right to Delete’ and similar regulations:
- Training & Policy Creation
Ensure employees are trained on how to set and implement data management policies. Proper training helps establish consistent procedures for identifying, handling and securely deleting personal data in compliance with regulatory requirements. - Maintaining Logs for Compliance
Keep detailed records of deletion requests and actions taken. Maintaining logs ensures traceability and simplifies compliance reporting, providing evidence of adherence to regulatory obligations during audits or investigations. - Ongoing Cyber Hygiene
Regularly update and maintain IT systems to keep them clean and organized. Proactive cyber hygiene practices, such as routine audits and data mapping, make it easier to locate and remove traces of personal data when needed, reducing the risk of errors and improving overall efficiency.
Achieve CCPA Compliance with BCWipe
For over 20 years, BCWipe has been trusted by the U.S. Department of Defense to securely wipe files and data remanence beyond forensic recovery. Compliant with key standards like the U.S. DoD 5220.22-M, IEEE 2883-2022 and NIST 800-88, BCWipe offers reliable data protection.
By choosing BCWipe, organizations gain access to advanced tools such as the Search feature and centralized management for remote wiping and software control.
Want to try out BCWipe and the new Search feature? Contact our Data Protection Specialist today to request a free trial or demo.
