



The use of encrypted laptop and desktop computers, as well as encrypted phones and external hard drives, is mandated by the Harvard Enterprise Security Policy (HESP) and Research Data Security Policy (HRDSP).
In accordance with university policies, everyone at Harvard is accountable for appropriately handling and encrypting confidential information stored on:
For the encryption of laptop and desktop computers, HESP and HRDSP recommend 6 tools:
Native Hardware Encryption
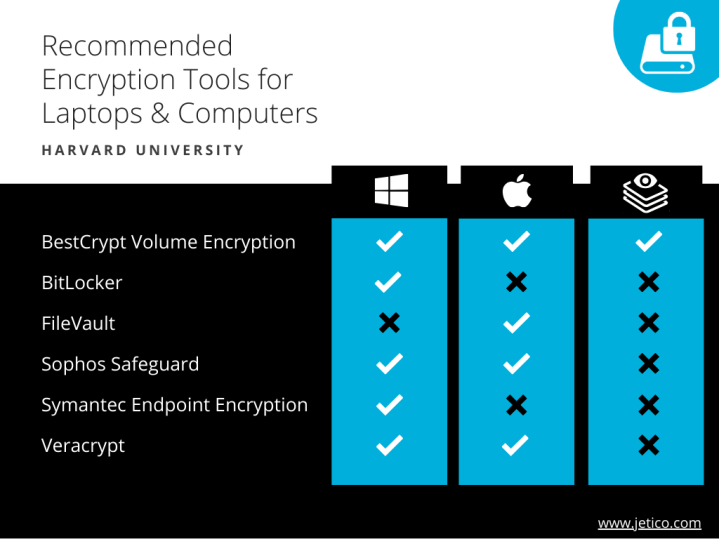
Third-Party Encryption Tools
Compared to native encryption, BestCrypt Volume Encryption provides:
Compared to third-party encryption tools:
Contact us today to learn more about BestCrypt Volume Encryption, schedule a demo or request a quote.
NOTE: The information provided in this article was retrieved from https://its.gse.harvard.edu/services/information-security/topics/encryption as of September 2023. We recommend visiting the Encryption page for the most up-to-date information, as the content may have been updated or changed since the time of this writing.