Computer Page
The computer page shows detailed information about selected client computer:
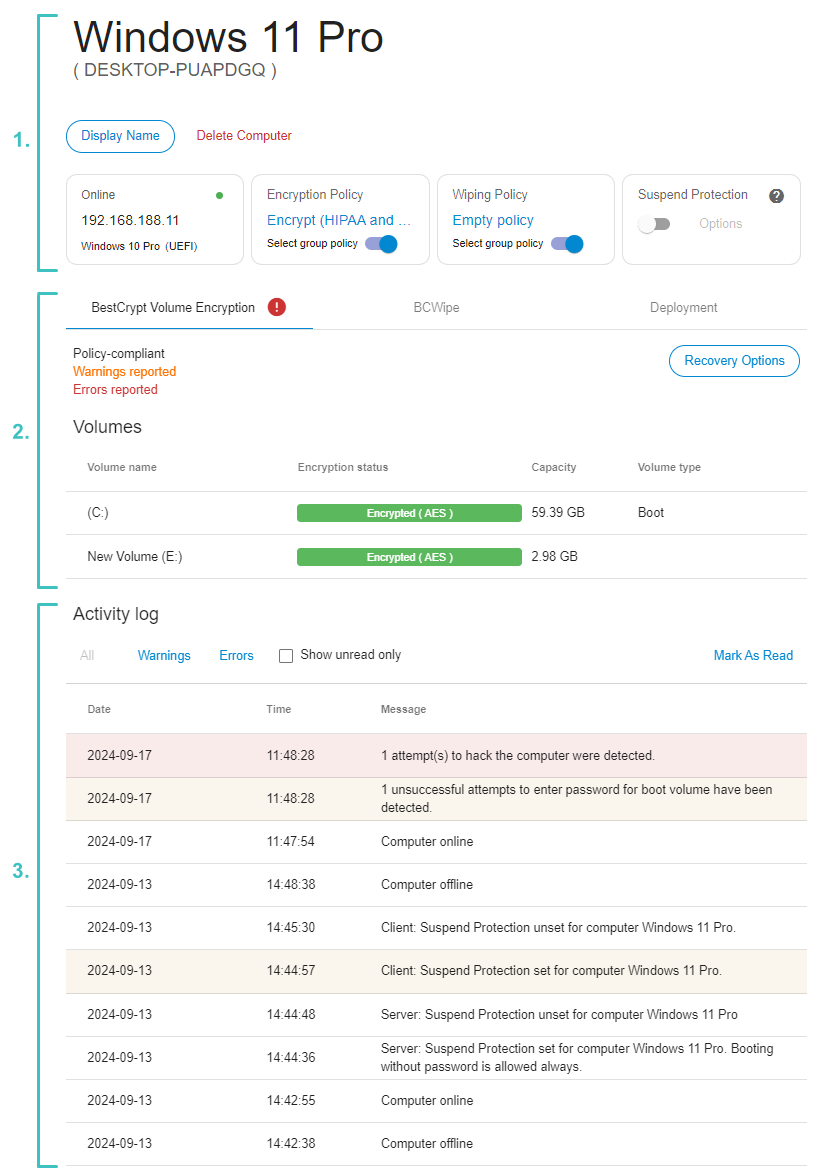
The page is divided into three parts:
General information (1)
This section incorporates the following information and controls:
- Computer name
By default, computer's hostname is displayed in this area. Additionally, a Display Name may be set to help distinguish between computers easier.
To set a Display Name, click the "Display Name" button. The Display Name will then replace the computer name, as shown in the screenshot above. The computer name will be displayed in brackets underneath the Display Name.
To get computers displayed by their Display Name in the left pane of the management console, enable "Show computers by display name" in Company Settings.
- Delete computer button
To remove the computer, click the "Delete Computer" button. Main article: Delete Computer
- Computer connection status
- Operating system and boot type (MBR/EFI)
- IP address
- Encryption policies
Choose whether computer should inherit a policy from a group it belongs to or use individual policy. Main article: Encryption policies
- Wiping policies
Choose whether computer should inherit a policy from a group it belongs to or use individual policy. Main article: Wiping policies
- Suspend protection
Temporarily disable boot-time prompt for password for troubleshooting or update roll-outs. Main article: Central Management of BestCrypt Volume Encryption
Software-specific information (2)
This section incorporates controls to manage BestCrypt Volume Encryption and BCWipe on the computer:
BestCrypt Volume Encryption tab:
- Information about policy compliance, warnings and errors
- Recovery options
Recover lost password or generate recovery information for encrypted computer or removable device. Main article: Rescue Procedures in Jetico Central Manager
- List of volumes
In this area the list of all volumes, fixed and removable attached to the computer is displayed.
For each volume a Volume Name, Encryption Status, displaying encryption progress in real time, Capacity and Volume Type are shown.
For removable media a unique ID is additionally displayed. This ID in recovery procedures for removable media.
BCWipe tab:
- Information about warnings and errors
- List of volumes
In this area the list of all volumes, fixed and removable attached to the computer is displayed.
For each volume, the amounts of Used Space, Browser History, User Activity, Reserved Space, and Free Space are displayed.
- Policy tasks
This area displays the wiping tasks contained in the applied wiping policy and their statuses. Main article: Wiping tasks
Deployment tab:
This area displays the versions of client software installed, the last update date, and options for the JCM administrator or operator to install/uninstall the software.
Activity log (3)
This area accumulates log messages from both Server and Client sides associated with this computer. The messages are divided in three categories:
Service messages - standard messages logging various settings being changed or updated.
Warning messages - medium importance messages, requiring attention, but not necessarily immediate action.
Error messages - high importance messages, requiring immediate action.
Clicking Warnings or Errors on top of the Activity Log will filter log messages by their importance. Checking Show unread will only leave the most recent messages in the view. Clicking Mark as read will reset the information about warnings and errors.
The Activity Log displays messages based on the currently active tab:
- If the BestCrypt Volume Encryption tab is active, all messages related to the BestCrypt Volume Encryption program are shown
- If the BCWipe tab is active, all messages related to the BCWipe program are shown
See also:
Central Management of BestCrypt Volume Encryption