Groups of Computers
JCM provides a convenient way for managing groups of computers. The first (default) group is created automatically by the setup program and is assigned the name New computers. This default group cannot be deleted. Newly added computers will appear in this group, unless the JCM Agent Setup file is launched with the special -G parameter.
There is no limit to the number of groups that can be created. However, the maximum number of computers in a single group is 100. Client computers can be distributed among these groups in any way deemed appropriate by the JCM administrator: by physical location, by required security policy, or by any other attribute. Both computer groups and the computers within each group are displayed in alphabetic order.
Encryption or wiping policies can be assigned to the entire group in bulk or through individual policies. A group policy is assigned on a Group page, whereas an individual policy is assigned on a Computer page. If an individual policy is assigned to a computer, the computer is marked with a 'gear' icon in the list.
If a group is selected in the left list, the Group page is displayed in the right pane. It looks like this:
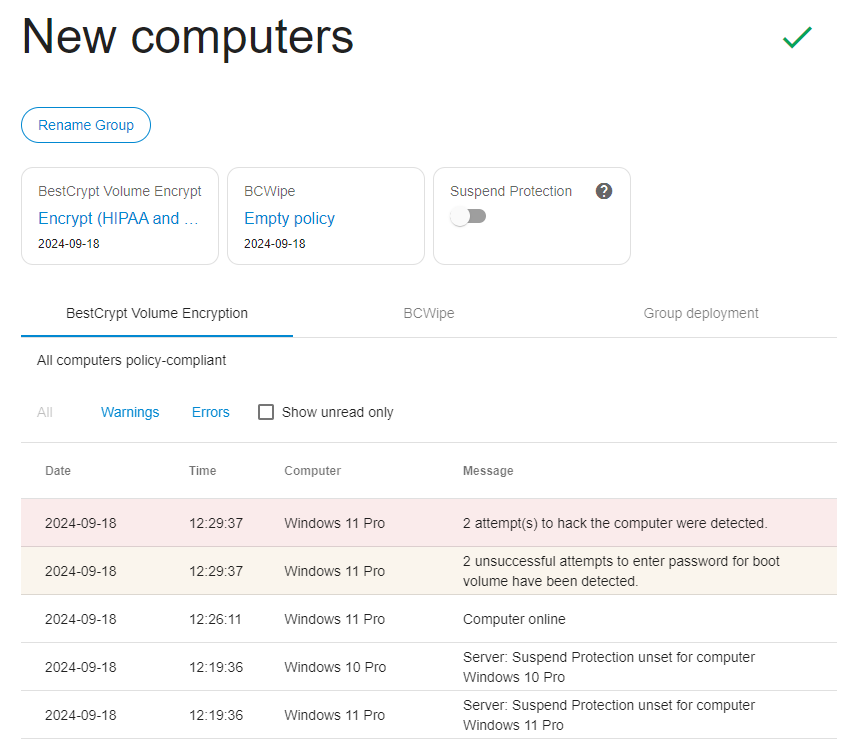
The page is divided into four sections:
- General information: The icon at the top left corner of the group page indicates current status of that group:
|
|
Green. Everything is in order. No action required. |
|
|
Yellow. Warnings reported for some client PCs. Check the computer page(s) for details. |
|
|
Red (excl.). Errors reported for some client PCs. Check the computer page(s) for details. |
To rename the group, click on the button "Rename Group" under the group name.
- Group Settings: this section displays software-specific settings and statistics for:
BestCrypt Volume Encryption
Encryption policy - review or change the encryption policy assigned to the group.
Suspend protection - temporarily disable boot-time prompt for password for all computers in the group (see Central Management of BestCrypt Volume Encryption for more details about the option).
Number of computers that are not policy compliant. You can see which computers are not compliant in the policy in the Computers and Groups table on the Company Page.
BCWipe
Wiping policy - review or change the wiping policy assigned to the group.
Status - displays a total number of errors or warnings currently reported for the computers in this group. Click on the hyperlink 'X errors reported' to view details.
- Activity Log: the log combines Activity Logs for all computers included in the group. Switch between BCWipe and BestCrypt Volume Encryption tabs to review the software-specific log messages. The log can be filtered to show only errors/warnings.
- Group deployment: the section hosts controls to control deployment of the client software in bulk.
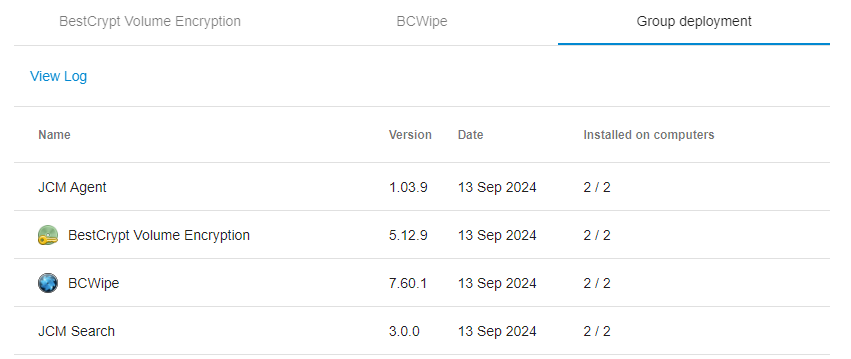
To push BCWipe or BestCrypt Volume Encryption to all computers in the group or to remove it, click Change next to the client software of choice. The following dialog pops up:
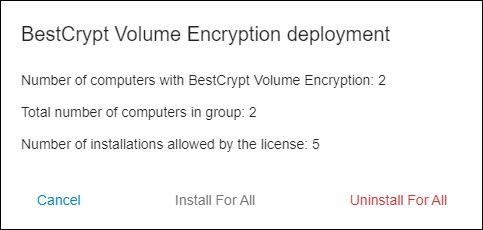
Depending on your use case, click either "Install for all" or "Uninstall for all" and follow further instructions.
Moving computers from one group to another
The Move function is available in the Computers and groups table on a company's page:
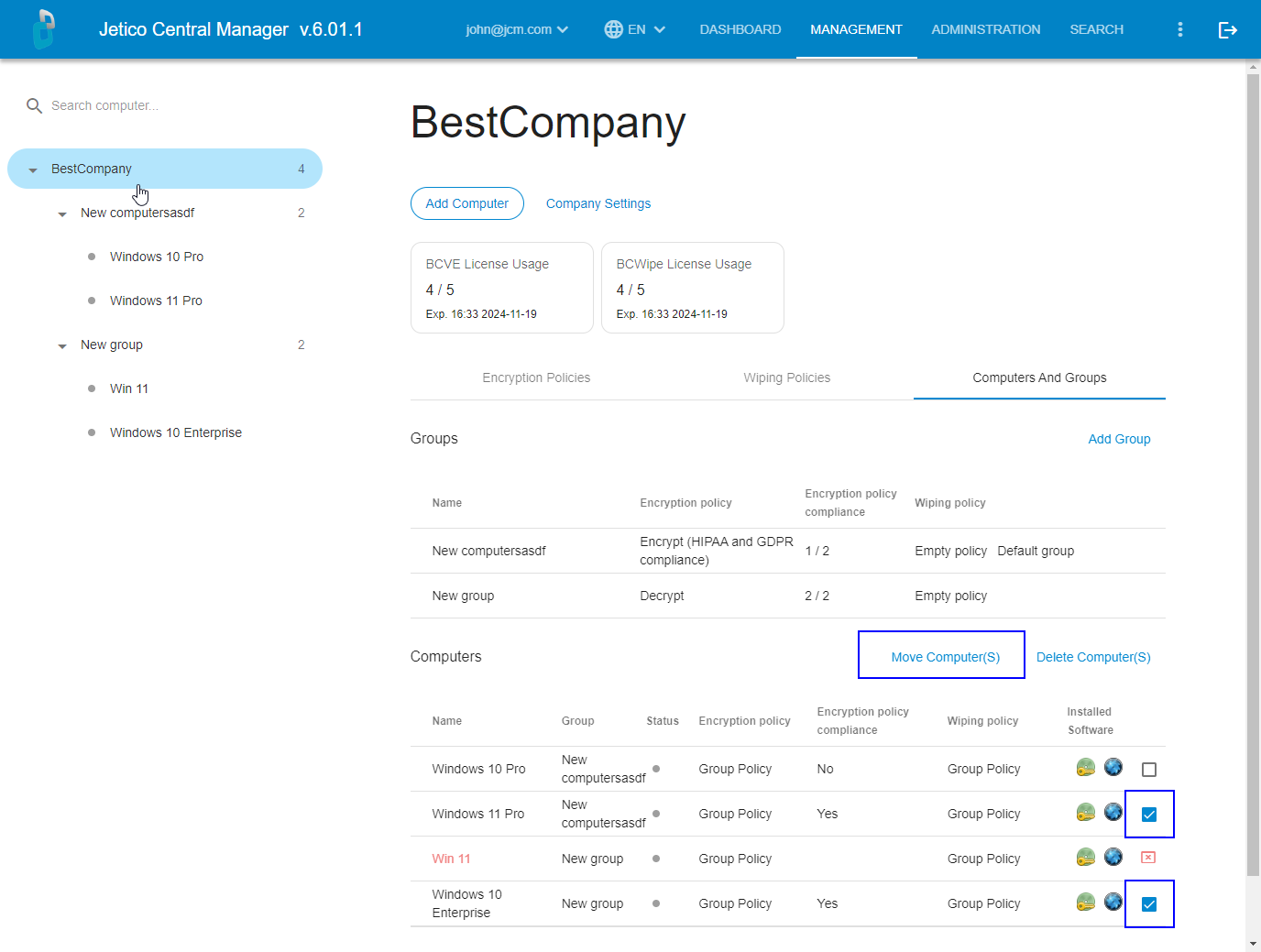
If a computer is moved from Group1 to Group2, the computer is automatically assigned the policy of Group2.
NOTE: (BestCrypt Volume Encryption): If the computer has already been encrypted and the 'move' operation would cause a change of encryption algorithm, the user will be prompted to decrypt the computer first and then attempt to move the computer again.
See also:


