Secure deletion of found data
One of the goals of searching for information on company computers is to identify data that appears on computers or storage devices where they should not be. If such data is found, the task of moving or deleting the data arises.
When you delete sensitive data, you shouldn't just delete it using the tools provided by the operating system. The usual "delete file" command deletes only the references to the file in the file system tables, without erasing the contents of the file from disk. As a result, the contents of the file can be restored, which should not have happened.
Instead of the usual "delete file" command, you should use the secure deletion (wiping) procedure. Jetico Central Manager (JCM) provides secure deletion of files and folders on remote client computers. When you find any information using JCM Search, one option is to securely delete some files.
After completing the search process, the JCM administrator will be able to securely delete (wipe) the found files.
Go to the "Search Result" tab and select the files that you want to delete by checking the boxes next to the corresponding files. The "Wipe Data" button will be available for clicking after at least one file has been selected for wiping.
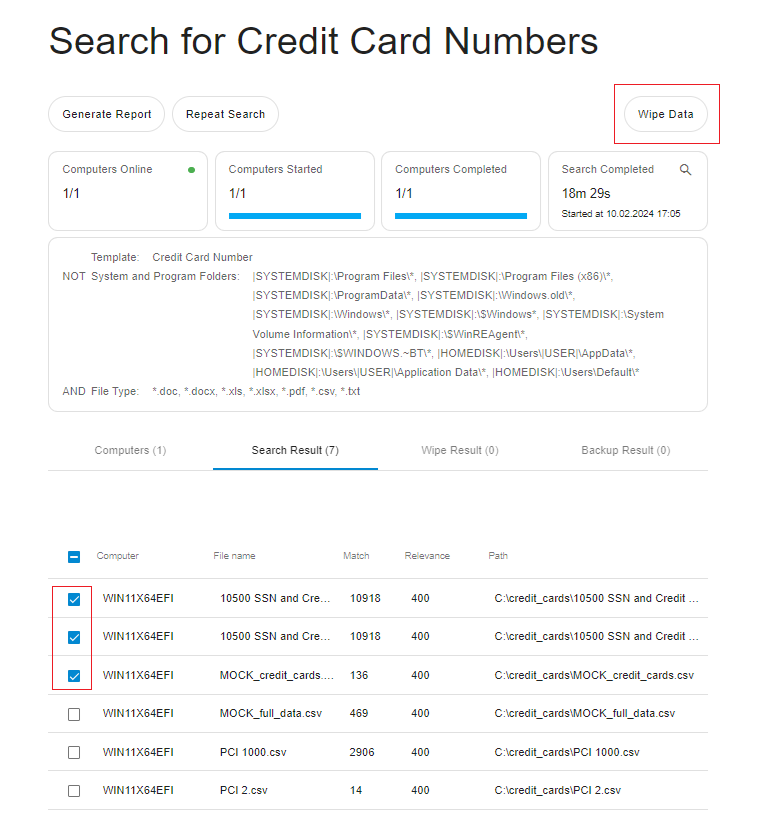
A window with wiping settings opens after clicking on the "Wipe Data" button.
Please note that there are a number of regulations regarding the proper secure deletion (wiping) of data. Usually the regulations are documented as state standards, for example "U.S. Department of Defense 5220.22-M(ECE)". The JCM BCWipe secure deletion program running on the client computer supports most (if not all) such standards. Each implementation of such a standard in the JCM software is called a "Wiping scheme".
You can select a wiping scheme and enable or disable the last pass verification before starting wiping. The list of available wiping schemes depends on your license.
It is also possible to create a backup copy of the data before securely deleting it. For more information about why a backup can be useful and how to automate its creation, read the article "Encrypted backup before secure deletion".
When you click on the "Wipe Data" button, the following form will appear:
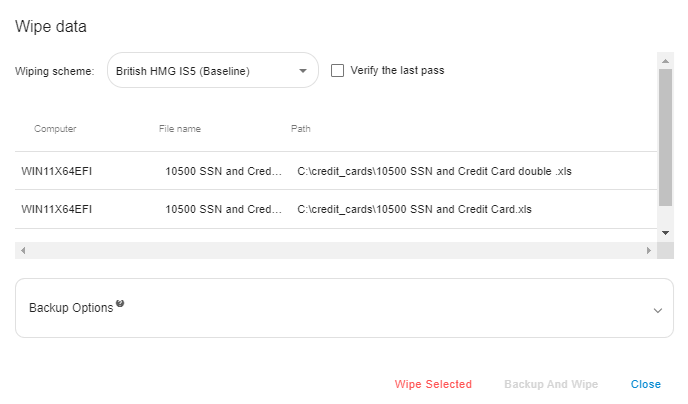
The wiping process will start after clicking the "Wipe Selected" button.
After starting the wiping process, the "Computers" tab will display its progress.
On the "Wipe Results" tab, you can monitor the status of each file selected for wiping in real time:
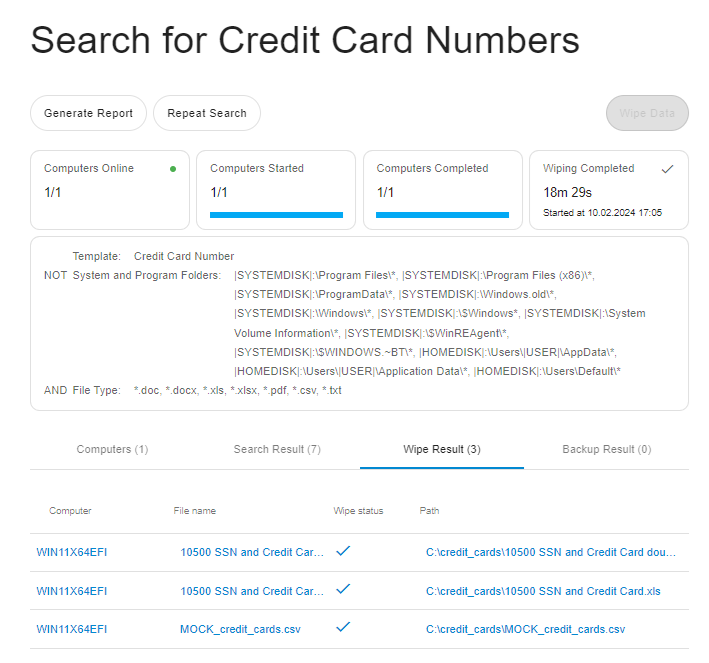
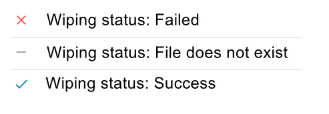
There are three possible wiping statuses for files:
A log button appears to the right of the wiping progress bar on the "Computers" tab after the wiping has started.
The log of the wiping process opens by clicking the log button:
After the wiping process is started, the "Show Log" button will appear on the "Computers" tab to the right of the wiping progress bar:
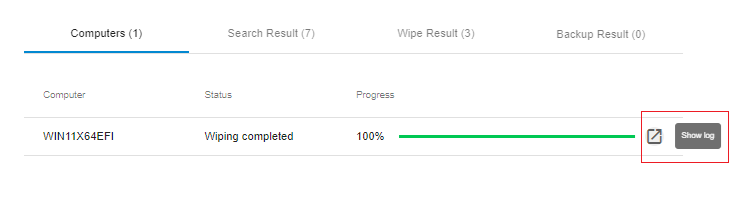
When you click the "Show Log" button, the wiping process log opens:
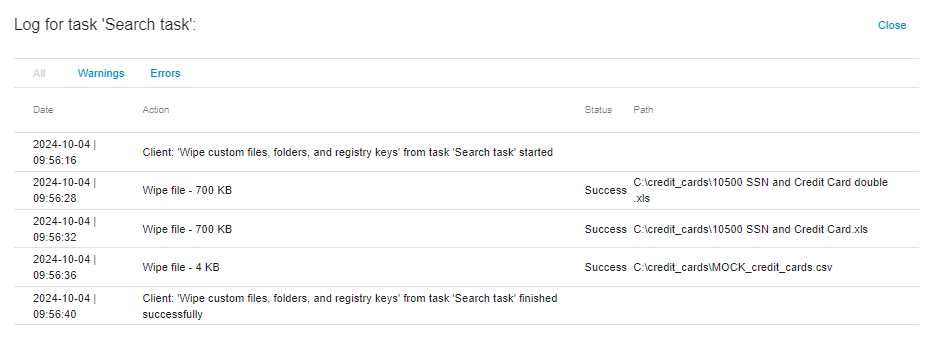
The log file can be viewed even if the wiping process has not yet been completed. Please note that to view the updated information in the log file, you should reopen it.
Read the article "Encrypted Backup before secure deletion" to get information about saving encrypted data before deleting it. This can be useful if you are not completely sure that the data on the computer will never be needed.