Using BestCrypt DataShelter
BestCrypt Data Shelter protects folders, therefore, the first step when using the program is to select the folder. Then the user should define a protection policy for the folder, i.e. the list of programs and users who have the right to access files in the folder.
|
|
|
|
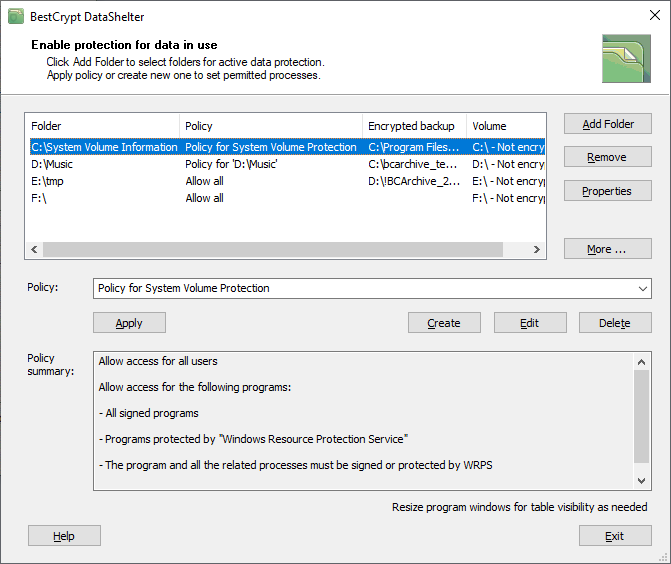
The picture above illustrates the main window of the program. It shows the list of protected folders with the policies assigned to them. The user can set an encrypted backup file for every folder and decide, should the disk volume where the folder is located be encrypted.
Protection policy defines the rules for the users and the programs.
Regarding the users, it is worth to think of allowing only your own account to access the folder. It is possible that there is a separate administrator account or other users who can access the computer. If someone attacks your computer, he/she will first of all attempt to get the administrator's credentials to be able to do everything in your system, or attack some user account with a weak password. But even getting the credentials, access to the folder will be denied for the attacker. So the attacker will be able to access the folder only by stealing your credentials, but not of someone else who perhaps has no so strong password.
For programs, there are two approaches:
- Allow all programs to access the folder, but set exclusions and forbid some of them from accessing the folder
- Select the programs that have the right to access the files in the folder, thus preventing all others from accessing the folder
The first approach can be useful when you exclude programs step by step, investigating how it affects your system and your normal work with the folder. On the other hand, the second approach can be more useful: you forbid access to the folder for all programs and then allow only selected programs to access it.
Defining the policy can be a straightforward process, because BestCrypt Data Shelter:
- Logs all the programs accessing the folder and then create a rule for the program from the log information
- Remembers the history of accessing the folders by the programs, so the policy can be created from the history
- The user can view the list of the programs installed on the computer, view properties of the programs and allow only a few of them to access the folder
- The program can list types of files in the folder and programs associated with the types of files. The user can choose only the associated programs for the protection policy
The user can update the policy when, for example, a new type of files appears in the folder and a new program should be allowed to access them.
BestCrypt Data Shelter notifies the user when it rejects an attempt of some program to access files in the folder. By clicking on the reference string in the notification dialog window the user can view more detailed information in the log file and change the rule for the program.
Optionally the program shows its icon in the system tray. The user can quickly run the program or view the log information from the system tray icon.
See also:
Encrypted backup of the folder
Creating policy based on folder access history