BestCrypt Control Panel
The BestCrypt Control Panel is the
central
BestCrypt-user interaction application. It allows you to perform
container creation and management (e.g., adding containers, changing
and removing passwords) as well as some advanced operations.
The following sections describe all functions of Control Panel
grouped together by the task they perform, starting with a general
overview of the main Control Panel window.
When you launch BestCrypt, the first thing you will see is the main
Control Panel window, consisting of a toolbar at the top of the window
and a number of control sections. Let's take a closer look at this
window:

Toolbar items
The Control Panel toolbar provides a set of items to help you access
different BestCrypt functions. Some of these functions apply only to
the selected container. The following controls are included: Create,
Locate, Mount, Eject, Forced eject, and Eject all.
- Create. This function launches a dialog to create, initialize and format a new BestCrypt container file. The Creating New Container section provides a detailed explanation of this function.
- Locate. This function enables you find an existing container file on your computer. Typically BestCrypt container files have a .jbc
extension, but any file can be interpreted as a BestCrypt container if
it has a minimum required size. This toolbar item allows you to add any
file to the container list and try to use it as a BestCrypt.
- Mount. This function will mount
the currently selected BestCrypt container. This toolbar item is
enabled only if the selected container is not already mounted.
- Eject.
This function ejects the currently selected BestCrypt container. This
toolbar item is enabled only if the selected container is already
mounted.
- Force Eject.
This function ejects the currently selected BestCrypt container
regardless of the fact that some of the files stored in this container
might be currently open in other applications. This action simulates
physical thumb drive removal and may result in corruption or loss of
the unsaved data and damage to the virtual disk file system structures.
However it guarantees that container will
be ejected in any case. Use it as an emergency measure only when you
urgently need to eject mounted container. This toolbar item is enabled
only if selected container is already mounted.
- Eject All. This toolbar item does the same as Force eject,
but for all currently mounted containers with the same possible side
effects. Consider this your "panic button" to immediately eject all
mounted containers in case of an emergency.
Container List
The leftmost area of the Control Panel's main window is called the container list. Each element in this list
corresponds to each container file known to be located on your system.
There are several ways how containers can end up in this list:
- Creating new containers. All newly
created
containers are added automatically to the Container List.
- Browsing for existing containers. Using
the Locate button on the toolbar or from
the BestCrypt main menu you can locate existing container files and add
them to the list.
- Mounting existing containers from Files.
You can mount containers by double-clicking on the container file in
Files. A container file mounted this way will be automatically added to the list if it was not there before.
Selected Container View
Selecting a container from the Container list by simply clicking on it enables a "Selected Container View" - an area on the right displaying general information about selected container, such as:
- File name. Selected container file name;
- Description.
Description text issued when container was created. This field is also
used to report a couple of special container states. For example, when
selected file is missing or is an invalid container file;
- Location. Path to the container file on your computer;
- Size.
Virtual encrypted disk size stored in a container file. Actual
container file size is always at least this size and typically a bit
more;
- Algorithm. Encryption algorithm, mode and
hash algorithm used to encrypt the data stored in the container file.
The values are divided with slashes: algorithm / mode / hash ;
- Mount point. Shows the location where selected container is currently mounted or "Not mounted" otherwise;
- Header encrypted.
If user encrypted the header of the container, or the header is
undefined, he/she will notice 'Encrypted or corrupted header' under the
Description string as the current status. In that case some of the
above fields are unavailable;
Menu bar combines groups of operations that can be
applied to the selected container into easily accessible menus. Each of
these groups is discussed separately in the following
sections of this guide, but for now let us briefly describe each group
and provide references for more information:
- File.
This menu groups Create Container, Locate Container, program Settings
and Exit commands.
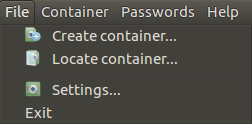
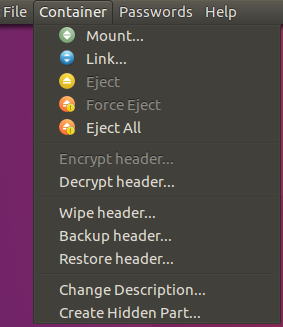
- Container. This menu groups commands
for the selected container. It includes Mount and Advanced container operations
sections which are
explained in detail further.
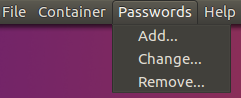
- Passwords. This menu groups together
commands that allow users to manag passwords for the selected container. Refer
to Managing container
passwords
section for more details.
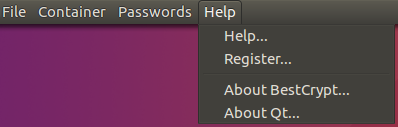
- Help. This menu combines Help,
Register, About BestCrypt and About Qt.
To create a new BestCrypt container, click the Create button on the welcome screen or on the toolbar.
The following dialog box will appear to guide you through the process:

Container
Creation Dialog incorporates the following fields and controls:
- File path. You may browse to the folder where you would like the container to be
created, or leave the default location and container name as is.
- Size. This group of controls allows you to specify the new encrypted volume size that will be stored in this containers.
- Size field. In this field you can enter a kilobyte, megabyte or gigabyte value depending on the size modifier setting.
- Size stepper. This stepper increases or decreases the value in the size field by 1.
- Size modifier menu. This popup menu presents several possible modifiers. Each modifier will convert the value in the size field to megabytes, gigabytes, terabytes or petabytes, correspondingly.
- Description. This optional field lets you enter a text
string with a maximum length of 20 characters to write a brief note or
provide a few words about the new container purpose, for example.
- Password and Confirm Password fields. Before continuing, you must create a new password and confirm it by retyping it correctly.
Click Create if you would like to use the default algorithm, hash or file system of the encrypted virtual disk. Otherwise, click Advanced and complete the next dialog:

The following fields and controls are available under Advanced settings
- Algorithm. Dropdown menu with all
available encryption algorithm. Default is "Rijndael (AES)".
- Mode. Drop-down menu with all
available encryption mode values for the encryption algorithm selected
above. Different algorithms support different subsets of encryption
modes. Recommended mode value is always set by default for each
algorithm you choose in the Algorithm menu
above.
- Format as. Drop-down menu containing
all file system formats supported by your system. New encrypted volume
will be formatted during the creation process using file system that
you specify here. The default value is ext3. It is recommended to use
"FAT" if you are planning to access this container on Mac or Windows
computers.
- New volume label. A volume label that
will be displayed when you mount the container.
- Mount new container. An option to automatically mount container after creation.
- Mount at specified location. Browse to the folder where you would like the container to be mounted by default.
Click Create to create a container with
the selected settings or click Next to head
to password options: 
- Key files. Browse to the files that will act as keyfiles. Refer to Keyfiles for further discussion.
- Header encryption. Encrypts the header so the container file will be harder to find on the file system. Refer to Header encryption for further discussion.
- Hash algorithm. Select the hash algorithm that will be used to encrypt your container password.
- Salt. Random data is generated for hash function, but you can regenerate it by clicking the Plus button.
- Iterations. The number of iterations to re-take hash from the initial hash.
Increasing the number will result in better security and require more
time to create a container and to mount it afterwards.
- Estimated mounting time. Estimated
time to process your password with all the settings selected above
before the container is mounted. This is also a time one brute-force
attack attempt will take on your container.
NOTE: Changing the default iteration count (16384)
prohibits further header encryption for the container. Likewise, if
Encrypt header option is checked, the Iterations box is automatically
set to default value and disabled.
Click Back to return to the previous page of the wizard.
Click Create to proceed with container creation.
BestCrypt initializes an encrypted volume inside the new container
with random data. This is needed to ensure the best level of protection
of the encrypted data. This operation might take a while; the progress
of the operation is displayed by the progress indicator. This operation
can be cancelled at any time by clicking the Cancel button.
After the process is complete your new container will be ready for
use. It will be
added to Container list with its' properties displayed in Selected
container view.
If you have set the Mount new container checkbox, the
container will also be mounted at this
point.
In addition to the
initial password container was created with, many more can be assigned
to each container. A total number of additional passwords depends on
container file format version and password type, but for the default
setting it is limited to 64 entries total (including any hidden part
passwords).
BestCrypt allows you to add, change and remove passwords for
existing containers and hidden parts. You can access these functions
from the Passwords
menu:

- Add. This operation allows
you to add a new password for your container. It will first ask for any
existing password and based on what is entered will either add another
main part or hidden part password. Hidden part or not, still only
unique passwords are allowed.
- Change. This operation allows
you to change any existing container password. New password value
should be unique.
- Remove. This
operation can remove existing container password completely so that
nobody can access container with that password anymore except for the
last main part password.
There is a pattern for how password management works for different
volume types (main or hidden). All password management operations will
first ask you to enter an existing container password. If that password
pertains to the main part, then, for example, a newly added password
will be added for the main part, and the other way around for each
possible hidden part.
For any new password, BestCrypt accepts any printable symbol in any language.
Anything you can type on your keyboard is a valid password symbol.
However, due to security considerations, the minimum password length is always at least 8 characters.
The maximum size is limited to 255 characters.
All container passwords must be unique. This includes passwords for the
main part and all possible hidden parts. For example, if you are adding
a new password for your hidden part but the same password is already
used for the main part, then this new password is considered a
duplicate and will be rejected.
BestCrypt provides many advanced functions to keep your data safe.
However, many of these functions require some familiarity with concepts
they represent.
They are easy to learn and will provide you with a better level of
understanding to perform these operations correctly and effectively and
employ them to your maximum advantage.
As always you can easily find all advanced functionality in the Container menu bar:

- Encrypt (or decrypt) header. This encrypts or decrypts container header to hide its known format and make it look like absolutely random data.
- Wipe header. This function completely deletes the header required to mount the
container. Note that you will need to provide a .kbb backup file to
mount the container afterwards.
- Backup header. This function safely creates a backup of all container service
information, including container header and encoded key data, into a
separate file. Any encryption keys or other secret information cannot
be read from a backup file without knowing the container password.
- Restore header. This restores all key data previously backed up in a separate file. Any
password changes made to the container after the backup was created
will be reverted.
- Change description. Allows to change
optional text description of the container.
- Create hidden part. This lets you create another encrypted volume in the container file and hide it in the free space of an existing main volume.
Most of these operations exist to boost the level of privacy when
using BestCrypt containers. The following section describes each one in more detail.
A BestCrypt container file consists of two different types of data:
- Encrypted data that is stored inside a container, and
- A service file header that contains all user-specified information
like container description, size and encryption algorithm specification.
Therefore, BestCrypt container file has a well-known structure that
can be
easily identified on your computer.
Sometimes it is unacceptable for anyone to know and prove that you have
a BestCrypt container file without actually knowing its password or
even asking for it.
Header encryption exists to avoid exactly this kind of threat.
The header encryption operation encrypts this well-known container
header to disguise it as random, nonsensical garbage; the entire
container file thus becomes absolutely indistinguishable from noise and
does not have any known structure anymore and ceases to have a
well-known structure.
Nobody, then, can unambiguously prove that this file is a BestCrypt
container.
However, it also means that even BestCrypt itself will not be able to
identify this file as a container. When you encrypt container header
and select it in container list BestCrypt
will not be able to display any information about it. Take a look at
the example below. Here we have selected a container with an encrypted
header:

To further reinforce your privacy, Control Panel also treats these
containers differently to remove any traces of their usage. For
example, when you add this container using the Locate button, it will be removed from the container list
when you close the Control Panel, thus hiding the fact that you even
tried to use this file (which, in any case, is filled with seemingly
random data) as a BestCrypt container.
To decrypt a container header and make it visible to BestCrypt again, return to the menu and select Decrypt header.
Header Backup
BestCrypt generates and securely stores a set of encryption keys
that all data in the container file is encrypted with. Each correct
container password is used to decode those keys and set up a virtual
encrypted disk. All data needed to check each password and decode
encryption keys is stored in a special section of the container file
that you can back up and safely store in a separate file without
copying the entire container file with all its encrypted data inside.
BestCrypt allows you to create these key data backup files with the .kbb extension by default, restore previous container states from them and use them to mount your container.
You can use these functions just as you would use most other Control Panel functions: from the Container menu

- Wipe header. This function completely deletes the header required to mount the
container. Note that you will need to provide a .kbb backup file to
mount the container afterwards.
- Backup header. This function safely creates a backup of all container service
information, including container header and encoded key data, into a
separate file. Any encryption keys or other secret information cannot
be read from a backup file without knowing the container password.
- Restore header. This restores all key data previously backed up in a separate file. Any
password changes made to the container after the backup was created
will be reverted.
To use key data backups effectively, there is an important point to
understand: backup files contain a copy of all information about
container encryption keys and passwords. This is of course stored in a
secure way, but the point is that by creating a backup file you have
created a snapshot of all passwords and encryption keys used for this
container.
Keep that in mind when you restore key data backup or mount a container
using it; in the former case the previous snapshot of all container
passwords is restored, and in the latter case you are authenticating
against this previous snapshot.
You can use this to your advantage by backing up all container
passwords in a separate backup file to safely store it on a remote
device and erase or encrypt this very same information in the actual
container file.
This way, the only means to mount such a container is by providing a
key data backup file stored separately.
Hidden Parts
All encrypted data stored inside a container looks like random
garbage until the correct encryption key is provided to properly
interpret it. BestCrypt takes care of all of this for you; all its asks
you to do is supply a password. However, there can be more than one
correct interpretation of this encrypted noise, provided you know
beforehand where to look for it and have the correct encryption key.
And that is the best part: When all your data looks like random
garbage, nobody can prove that you have more than one interpretation of
it in another subset of data hidden among this random noise.
This is precisely what the hidden part is:
A secret subset of encrypted data hidden inside existing encrypted (or
random) data that can be made sense of only if you know where to look
and have the correct password. Nobody else can prove that it really
exists and force you to submit any passwords for it.
In cryptography, this concept is called plausible deniability or deniable encryption
and is best explained by an example:
Imagine a situation when you are pressed hard to reveal your container
password. If you store all of your very important data inside a hidden
part and fill the main part with seemingly and convincingly important
(but really just decoy) data you can, after some hesitation, reveal the
password for the main decoy part of your container and convincingly deny
the existence of any other encrypted data besides the one that you've
just revealed to your interrogators. And BestCrypt, of course, makes
sure that it is impossible to prove you have anything else besides the
main decoy part.
Being a powerful feature, Hidden Parts requires some caution to use properly.
Because BestCrypt does not know about any hidden parts you might
have when mounting the main part of your container, any changes you
make to the mounted main part can overwrite and damage the hidden part.
You are strongly advised to fill your main part with all decoy data
before creating any hidden parts.
When you choose to create a new hidden part you will be greeted by the New Hidden Part dialog, shown below:

- Protect existing hidden part. If you already have any existing hidden parts in this container, this
button will allow you to enter their passwords and take the space they
occupy into account when creating another hidden part. Maximum
available space will be corrected and BestCrypt will make sure a new
hidden part will not use the space occupied by existing hidden parts.
- Format as. As in the Create New Container dialog this pop-up menu
allows you to choose the filesystem your new hidden part will be
formatted in. Default value is chosen "ext3" file system. If
you want the container to be supported on Windows and Linux computers,
choose "FAT" option.
- Mount new hidden part. Activate this option if you want your new hidden part to be mounted automatically after creation.
- New hidden part size. This group of controls allows you to specify the size of your new
hidden part much like you specified the size of the container in the Create New Container
dialog. The only difference is that the size of the new hidden part is
limited by the available free space inside your container's main part.
- Size slider. The slider's maximum value is set to the
maximum available size for new hidden part in megabytes. Moving the
slider, you can adjust the size of the new hidden part relative to
maximum size.
- Size field. This field shows the current exact value of the new hidden part size
in megabytes. You can directly input your own values in it and new
relative to maximum size will be updated with the Size slider.
- Size stepper. This stepper increases or decreases the new hidden part size by 1 megabyte.
- Create. Starts the creation process
using all specified preferences.
Click the Create button to add and format new hidden part once you've set all preferences and protected any and all existing hidden parts.
You will be asked to supply an initial password for your new hidden part.
After creation completes you can work with your new hidden part as
usual. All container operations described in this guide apply to the
hidden parts in the same way they apply to the main part, with a couple
of exceptions:
- You cannot create a new hidden part inside an existing hidden part,
although you can have multiple hidden parts within a common main part.
- Any hidden part information, like size and users, are never shown in the selected container view.
See also:
Basic concepts
Strong password guidelines
















