Creating policy manually
When BestCrypt Data Shelter protects folders from unwanted programs and users, it applies some Protection Policy to the folder. The user can create such a policy keeping in mind a concrete folder, or create the policy from general considerations.
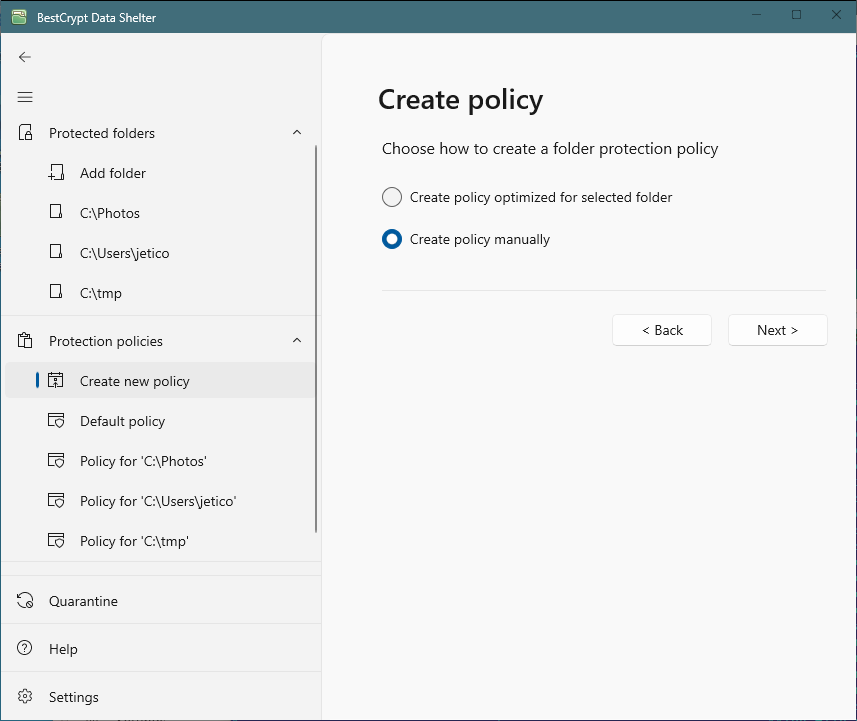
To create new protection policy from scratch click Create new policy from the Protection policies menu in the left pane of the program window. The following window will appear.
|
|
|
|
Select Create policy manually radio button and click the Next button to continue. The following window will appear.
|
|
|
|
If you want to allow all the users to access the folder, set the All users radio button. To forbid access to the folder for some user, remove check mark from the corresponding user in the All users tree view.
Chapter Using BestCrypt Data Shelter explains the idea of selecting only a few user accounts for accessing the folder. For example, you allow only your own user account to access the folder. If the attacker is able to access your computer, he/she should steal exactly your user name and password to read the contents of the protected folder, not any system embedded or default "Administrator" account.
Chapter Using BestCrypt Data Shelter explains also two approaches of allowing All programs to access the folders with exceptions, or allow only Selected programs to access the folder. When you choose the Selected programs option, you can list the programs explicitly by checking or unchecking them from the Included programs tree view control. Since not absolutely all executable files on your computer can appear in the list, it is possible to include the one manually to the list by right-clicking the Included programs tree view control and browsing the file.
Besides listing the trusted programs one by one, you can select a class of programs allowed to access the folder. Click the All signed programs option to allow securely signed executables to read files in the folder. As explained in the Code signing article: "Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted since it was signed". So by setting the All signed programs option you will trust the vendors who securely signed their software to guarantee that their programs will not contain code harmful to your data.
A number of the Windows operating system embedded components are protected by "Windows Resource Protection Service" (WRPS). Although it is not absolutely necessary for these utilities to access all files in all folders, you can allow them to access your protected folder by setting the Programs protected by the "Windows Resource Protection Service" (WRPS) option. Please note that when you look at the list of programs in various BestCrypt Data Shelter lists, you may pay attention to the columns Signed and WRPS protected. Surprisingly, some WRPS programs are not securely signed by Microsoft (that we would highly expect), and it is the reason why the WRPS option exists as a separate option in BestCrypt Data Shelter.
Note also that you can inspect a detailed information about some program in the list by right-clicking on it in the list and running the Properties command from appeared context menu.
Chapter Protection policy overview explains the option All the related processes must be signed or protected by WRPS. BestCrypt Data Shelter monitors communications between processes (read also What is BestCrypt Data Shelter article). BestCrypt Data Shelter remembers information about parents and grandparents of all the processes. It detects and remembers events of opening the process by other processes. So if you allow some program to access the folder, by setting the option you will also require that all the interprocess communications with the program should happen only with trusted and signed programs.
You may decide that it should not be possible to copy the files from the protected folder outside the folder. In this case check the Do not allow processes to copy files from a protected folder checkbox.
Finally, if you choose to use all the possible settings for the protection policy, it can look like the following picture illustrates. Click the Save policy button to save the protection policy.
|
|
|
|
See also: